|
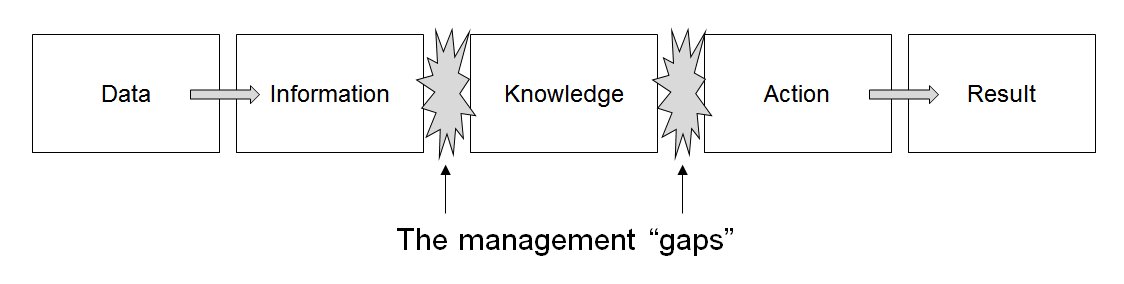
Data Management
Data management comprises all disciplines related to handling data as a valuable resource, it is the practice of managing an organization's data so it can be analyzed for decision making. Concept The concept of data management emerged alongside the evolution of computing technology. In the 1950s, as computers became more prevalent, organizations began to grapple with the challenge of organizing and storing data efficiently. Early methods relied on punch cards and manual sorting, which were labor-intensive and prone to errors. The introduction of database management systems in the 1970s marked a significant milestone, enabling structured storage and retrieval of data. By the 1980s, relational database models revolutionized data management, emphasizing the importance of data as an asset and fostering a data-centric mindset in business. This era also saw the rise of data governance practices, which prioritized the organization and regulation of data to ensure quality and complian ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Academic Disciplines
An academic discipline or field of study is a branch of knowledge, education, taught and researched as part of higher education. A scholar's discipline is commonly defined by the faculty (division), university faculties and learned society, learned societies to which they belong and the academic journals in which they publish research. Disciplines vary between well-established ones in almost all universities with well-defined rosters of journals and conferences and nascent ones supported by only a few universities and publications. A discipline may have branches, which are often called sub-disciplines. The following Outline (list), outline provides an overview of and topical guide to academic disciplines. In each case, an entry at the highest level of the hierarchy (e.g., Humanities) is a group of broadly similar disciplines; an entry at the next highest level (e.g., Music) is a discipline having some degree of autonomy and being the fundamental identity felt by its scholars. L ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data
Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted formally. A datum is an individual value in a collection of data. Data are usually organized into structures such as tables that provide additional context and meaning, and may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data are commonly used in scientific research, economics, and virtually every other form of human organizational activity. Examples of data sets include price indices (such as the consumer price index), unemployment rates, literacy rates, and census data. In this context, data represent the raw facts and figures from which useful information can be extracted. Data are collected using technique ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decision-making
In psychology, decision-making (also spelled decision making and decisionmaking) is regarded as the Cognition, cognitive process resulting in the selection of a belief or a course of action among several possible alternative options. It could be either Rationality, rational or irrational. The decision-making process is a reasoning process based on assumptions of value (ethics and social sciences), values, preferences and beliefs of the decision-maker. Every decision-making process produces a final choice, which may or may not prompt action. Research about decision-making is also published under the label problem solving, particularly in European psychological research. Overview Decision-making can be regarded as a Problem solving, problem-solving activity yielding a solution deemed to be optimal, or at least satisfactory. It is therefore a process which can be more or less Rationality, rational or Irrationality, irrational and can be based on explicit knowledge, explicit or tacit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Management Association
The Data Management Association (DAMA), formerly known as the Data Administration Management Association, is a global not-for-profit organization which aims to advance concepts and practices about information management and data management. It describes itself as vendor-independent, all-volunteer organization, and has a membership consisting of technical and business professionals. Its international branch is called ''DAMA International'' (or ''DAMA-I''), and DAMA also has various continental and national branches around the world. History The Data Management Association International was founded in 1980 in Los Angeles. Other early chapters were:San Francisco, Portland, Seattle, Minneapolis, NewYork, and Washington D.C. Data Management Body of Knowledge DAMA has published the Data Management Body of Knowledge (DMBOK), which contains suggestions on best practices and suggestions of a common vernacular for enterprise data management. The first edition (DAMA-DMBOK) was publishe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Asset
Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted formally. A datum is an individual value in a collection of data. Data are usually organized into structures such as tables that provide additional context and meaning, and may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data are commonly used in scientific research, economics, and virtually every other form of human organizational activity. Examples of data sets include price indices (such as the consumer price index), unemployment rates, literacy rates, and census data. In this context, data represent the raw facts and figures from which useful information can be extracted. Data are collected using techniques such as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
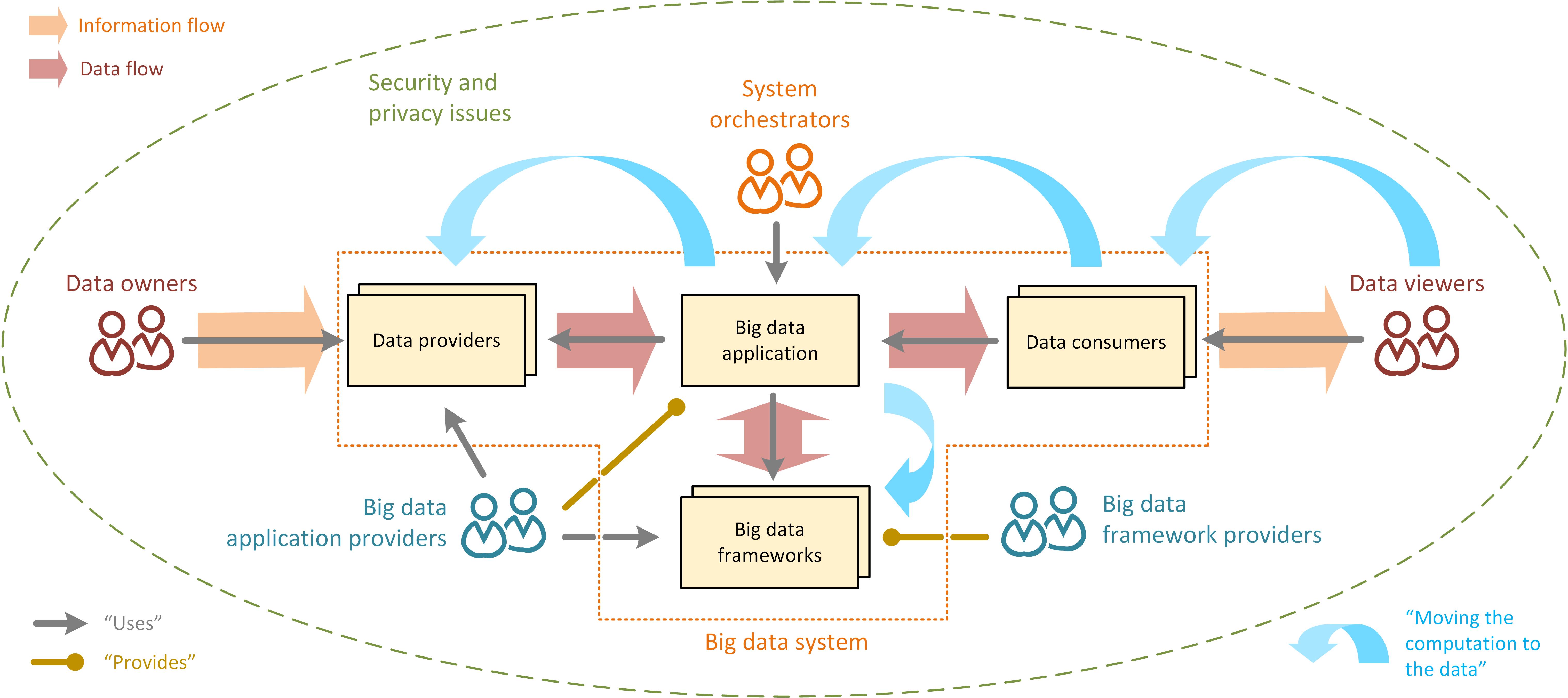
Big Data
Big data primarily refers to data sets that are too large or complex to be dealt with by traditional data processing, data-processing application software, software. Data with many entries (rows) offer greater statistical power, while data with higher complexity (more attributes or columns) may lead to a higher false discovery rate. Big data analysis challenges include Automatic identification and data capture, capturing data, Computer data storage, data storage, data analysis, search, Data sharing, sharing, Data transmission, transfer, Data visualization, visualization, Query language, querying, updating, information privacy, and data source. Big data was originally associated with three key concepts: ''volume'', ''variety'', and ''velocity''. The analysis of big data presents challenges in sampling, and thus previously allowing for only observations and sampling. Thus a fourth concept, ''veracity,'' refers to the quality or insightfulness of the data. Without sufficient investm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
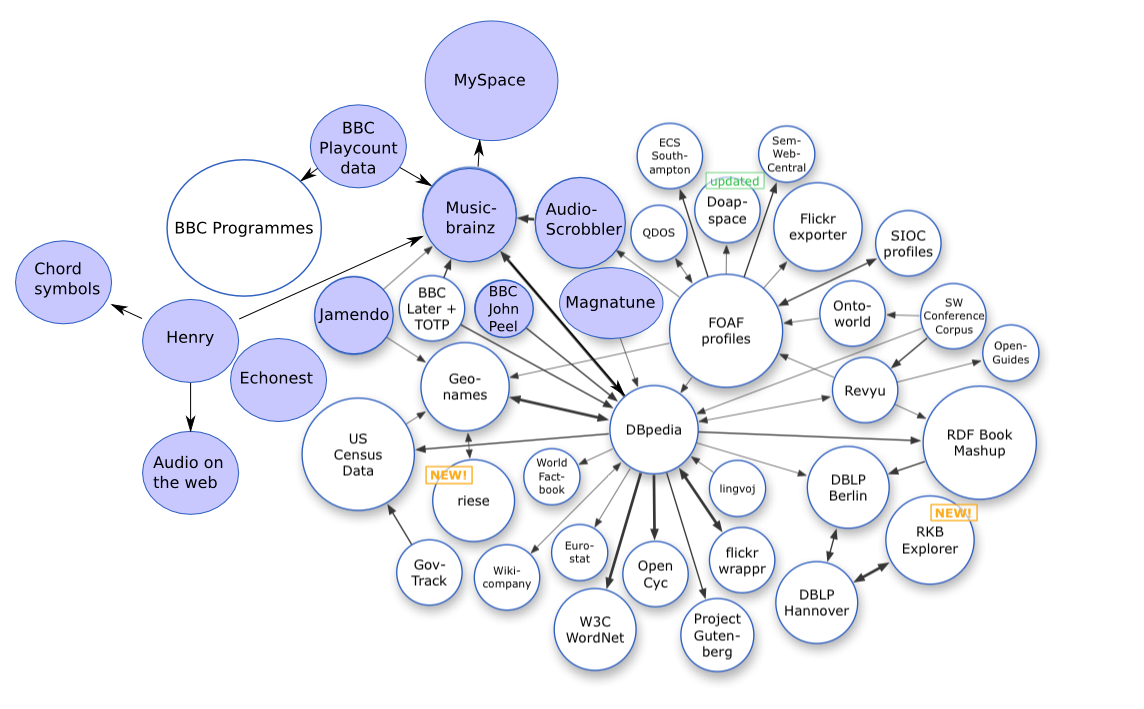
Open Data
Open data are data that are openly accessible, exploitable, editable and shareable by anyone for any purpose. Open data are generally licensed under an open license. The goals of the open data movement are similar to those of other "open(-source)" movements such as open-source software, open-source hardware, open content, open specifications, open education, open educational resources, open government, open knowledge, open access (publishing), open access, open science, and the open web. The growth of the open data movement is paralleled by a rise in intellectual property rights. The philosophy behind open data has been long established (for example in the Merton thesis, Mertonian tradition of science), but the term "open data" itself is recent, gaining popularity with the rise of the Internet and World Wide Web and, especially, with the launch of open-data government initiatives Data.gov, Data.gov.uk and Data.gov.in. Open data can be linked data—referred to as linked open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Curation
Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted formally. A datum is an individual value in a collection of data. Data are usually organized into structures such as tables that provide additional context and meaning, and may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data are commonly used in scientific research, economics, and virtually every other form of human organizational activity. Examples of data sets include price indices (such as the consumer price index), unemployment rates, literacy rates, and census data. In this context, data represent the raw facts and figures from which useful information can be extracted. Data are collected using techniques suc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Retention
Data retention defines the policies of persistent data and records management for meeting legal and business data archival requirements. Although sometimes interchangeable, it is not to be confused with the Data Protection Act 1998. The different data retention policies weigh legal and privacy concerns economics and need-to-know concerns to determine the retention time, archival rules, data formats, and the permissible means of storage, access, and encryption. Implementation In the field of telecommunications, "data retention" generally refers to the storage of call detail records (CDRs) of telephony and internet traffic and transaction data ( IPDRs) by governments and commercial organisations. In the case of government data retention, the data that is stored is usually of telephone calls made and received, emails sent and received, and websites visited. Location data is also collected. The primary objective in government data retention is traffic analysis and mass surve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |