|
DB Networks
DB Networks is a privately held Information Security company founded in the United States The company is headquartered in San Diego, California, and its regional offices are located in Palo Alto, California and Seattle, Washington. In May 2018, DB Networks announced that it will change its company name to DB CyberTech. History DB Networks was founded in United States in 2009 to provide database security including database infrastructure assessment, compromised credential identification, and SQL injection defense, predominantly to the financial services industry and federal government. The company was initially financed by Angel investors. In 2012 the company raised $4.5M in venture capital from Khosla Ventures. In 2014 the company closed a $17 Million round of funding led by Khosla Ventures and Grotech Ventures. The company's first product, the ADF-4200, was launched in February 2013. Also in February 2013 the company announced a partnership with Alamo City Engineering Service ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
San Diego, California
San Diego ( , ; ) is a city on the Pacific Ocean coast of Southern California located immediately adjacent to the Mexico–United States border. With a 2020 population of 1,386,932, it is the eighth most populous city in the United States and the seat of San Diego County, the fifth most populous county in the United States, with 3,338,330 estimated residents as of 2019. The city is known for its mild year-round climate, natural deep-water harbor, extensive beaches and parks, long association with the United States Navy, and recent emergence as a healthcare and biotechnology development center. San Diego is the second largest city in the state of California, after Los Angeles. Historically home to the Kumeyaay people, San Diego is frequently referred to as the "Birthplace of California", as it was the first site visited and settled by Europeans on what is now the U.S. west coast. Upon landing in San Diego Bay in 1542, Juan Rodríguez Cabrillo claimed the area for Spain, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Maryland, Baltimore County
The University of Maryland, Baltimore County (UMBC) is a public research university in Baltimore County, Maryland. It has a fall 2022 enrollment of 13,991 students, 61 undergraduate majors, over 92 graduate programs (38 master, 25 doctoral, and 29 graduate certificate programs) and the first university research park in Maryland. It is classified among "R1: Doctoral Universities – Very High Research Activity". Established as a part of the University System of Maryland in 1966, the university became the first public college or university in Maryland to be inclusive of all races. UMBC has the fourth highest enrollment of the University System of Maryland, specializing in natural sciences and engineering, as well as programs in the liberal arts and social sciences. Athletically, the UMBC Retrievers have 17 NCAA Division I teams that participate in the America East Conference. History The planning of the University of Maryland, Baltimore County was first discussed in the 19 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Forensics
Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery, investigation, examination and analysis of material found in digital devices, often in relation to mobile devices and computer crime. The term digital forensics was originally used as a synonym for computer forensics but has expanded to cover investigation of all devices capable of storing digital data. With roots in the personal computing revolution of the late 1970s and early 1980s, the discipline evolved in a haphazard manner during the 1990s, and it was not until the early 21st century that national policies emerged. Digital forensics investigations have a variety of applications. The most common is to support or refute a hypothesis before criminal or civil courts. Criminal cases involve the alleged breaking of laws that are defined by legislation and that are enforced by the police and prosecuted by the state, such as murder, theft and assault agai ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized/inappropriate access to data, or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g. electronic or physical, tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves: * identifying inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
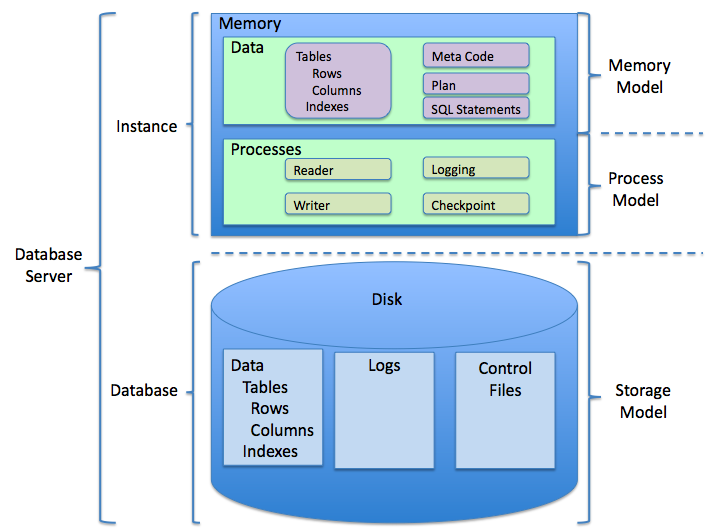
Relational Database
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as relati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Appliance
A virtual appliance is a pre-configured virtual machine image, ready to run on a hypervisor; virtual appliances are a subset of the broader class of software appliances. Installation of a software appliance on a virtual machine and packaging that into an image creates a virtual appliance. Like software appliances, virtual appliances are intended to eliminate the installation, configuration and maintenance costs associated with running complex stacks of software. A virtual appliance is not a complete virtual machine platform, but rather a software image containing a software stack designed to run on a virtual machine platform which may be a Type 1 or Type 2 hypervisor. Like a physical computer, a hypervisor is merely a platform for running an operating system environment and does not provide application software itself. Many virtual appliances provide a Web page user interface to permit their configuration. A virtual appliance is usually built to host a single application; it the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Appliance
A security appliance is any form of server appliance that is designed to protect computer networks from unwanted traffic. Types of Security Appliances * Active devices block unwanted traffic. Examples of such devices are firewalls, anti virus scanning devices, and content filtering devices. * Passive devices detect and report on unwanted traffic, such as intrusion detection appliances. * Preventative devices scan networks and identify potential security problems (such as penetration testing and vulnerability assessment appliances). * Unified Threat Management (UTM) appliances combine features together into one system, such as some firewalls, content filtering, web caching A Web cache (or HTTP cache) is a system for optimizing the World Wide Web. It is implemented both client-side and server-side. The caching of multimedias and other files can result in less overall delay when browsing the Web. Parts of the syste ... etc. References Server appliance {{compu-network-s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Threat Intelligence
Cyber threat intelligence (CTI) is knowledge, skills and experience-based information concerning the occurrence and assessment of both cyber and physical threats and threat actors that is intended to help mitigate potential attacks and harmful events occurring in cyberspace. Cyber threat intelligence sources include open source intelligence, social media intelligence, human Intelligence, technical intelligence, device log files, forensically acquired data or intelligence from the internet traffic and data derived for the deep and dark web. In recent years, threat intelligence has become a crucial part of companies' cyber security strategy since it allows companies to be more proactive in their approach and determine which threats represent the greatest risks to a business. This puts companies on a more proactive front - actively trying to find their vulnerabilities and prevents hacks before they happen. This method is gaining importance in recent years since, as IBM estimates, the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero-day (computing)
A zero-day (also known as a 0-day) is a computer-software vulnerability previously unknown to those who should be interested in its mitigation, like the vendor of the target software. Until the vulnerability is mitigated, hackers can exploit it to adversely affect programs, data, additional computers or a network. An exploit taking advantage of a zero-day is called a zero-day exploit, or zero-day attack. The term "zero-day" originally referred to the number of days since a new piece of software was released to the public, so "zero-day software" was obtained by hacking into a developer's computer before release. Eventually the term was applied to the vulnerabilities that allowed this hacking, and to the number of days that the vendor has had to fix them. Once the vendors learn of the vulnerability, they will usually create patches or advise workarounds to mitigate it. The more recently that the vendor has become aware of the vulnerability, the more likely it is that no fix or mit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Whitelist
A whitelist, allowlist, or passlist is a mechanism which explicitly allows some identified entities to access a particular privilege, service, mobility, or recognition i.e. it is a list of things allowed when everything is denied by default. It is the opposite of a blacklist, which is a list of things denied when everything is allowed by default. Email whitelists Spam filters often include the ability to "whitelist" certain sender IP addresses, email addresses or domain names to protect their email from being rejected or sent to a junk mail folder. These can be manually maintained by the user or system administrator - but can also refer to externally maintained whitelist services. Non-commercial whitelists Non-commercial whitelists are operated by various non-profit organisations, ISPs, and others interested in blocking spam. Rather than paying fees, the sender must pass a series of tests; for example, their email server must not be an open relay and have a static IP address. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blacklist (computing)
In computing, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs, IP addresses, domain names, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed. Blacklists can be applied at various points in a security architecture, such as a host, web proxy, DNS servers, email server, firewall, directory servers or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking malicious fil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scientific Modeling
Scientific modelling is a scientific activity, the aim of which is to make a particular part or feature of the world easier to understand, define, quantify, visualize, or simulate by referencing it to existing and usually commonly accepted knowledge. It requires selecting and identifying relevant aspects of a situation in the real world and then developing a model to replicate a system with those features. Different types of models may be used for different purposes, such as conceptual models to better understand, operational models to operationalize, mathematical models to quantify, computational models to simulate, and graphical models to visualize the subject. Modelling is an essential and inseparable part of many scientific disciplines, each of which has its own ideas about specific types of modelling. The following was said by John von Neumann. There is also an increasing attention to scientific modelling in fields such as science education, philosophy of science, sys ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)