|
Dumper (computer Program)
In computer programming, a dumper is a program which copies data from one source (usually a proprietary format) to another (usually in a more easily accessible format). A dumper is a program that saves data from the computer's memory, usually from a foreign process (program) to a (*.dmp) file. Often the process's memory is dumped automatically to disk if the program crashes. You may recover any unsaved data from this file or send it to the developer so he can investigate what caused the crash. Another use of 'dumpers' can be dumping Windows Exe-files from memory after they have been unpacked/ decrypted for further analysis (in case of malware), or after unwrapping/unpacking certain security envelopes. These security envelopes are applied by the developer or software vendor to 'protect' these applications. Usually, a security envelope checks if the application has not been modified, if you are still on your evaluation period or if the original CD is inserted before it unpacks and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Programming
Computer programming is the process of performing a particular computation (or more generally, accomplishing a specific computing result), usually by designing and building an executable computer program. Programming involves tasks such as analysis, generating algorithms, profiling algorithms' accuracy and resource consumption, and the implementation of algorithms (usually in a chosen programming language, commonly referred to as coding). The source code of a program is written in one or more languages that are intelligible to programmers, rather than machine code, which is directly executed by the central processing unit. The purpose of programming is to find a sequence of instructions that will automate the performance of a task (which can be as complex as an operating system) on a computer, often for solving a given problem. Proficient programming thus usually requires expertise in several different subjects, including knowledge of the application domain, specialized algori ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Format
A file format is a standard way that information is encoded for storage in a computer file. It specifies how bits are used to encode information in a digital storage medium. File formats may be either proprietary or free. Some file formats are designed for very particular types of data: PNG files, for example, store bitmapped images using lossless data compression. Other file formats, however, are designed for storage of several different types of data: the Ogg format can act as a container for different types of multimedia including any combination of audio and video, with or without text (such as subtitles), and metadata. A text file can contain any stream of characters, including possible control characters, and is encoded in one of various character encoding schemes. Some file formats, such as HTML, scalable vector graphics, and the source code of computer software are text files with defined syntaxes that allow them to be used for specific purposes. Specifications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Program
A computer program is a sequence or set of instructions in a programming language for a computer to execute. Computer programs are one component of software, which also includes documentation and other intangible components. A computer program in its human-readable form is called source code. Source code needs another computer program to execute because computers can only execute their native machine instructions. Therefore, source code may be translated to machine instructions using the language's compiler. ( Assembly language programs are translated using an assembler.) The resulting file is called an executable. Alternatively, source code may execute within the language's interpreter. If the executable is requested for execution, then the operating system loads it into memory and starts a process. The central processing unit will soon switch to this process so it can fetch, decode, and then execute each machine instruction. If the source code is requested for execution, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer File
A computer file is a computer resource for recording data in a computer storage device, primarily identified by its file name. Just as words can be written to paper, so can data be written to a computer file. Files can be shared with and transferred between computers and mobile devices via removable media, networks, or the Internet. Different types of computer files are designed for different purposes. A file may be designed to store an Image, a written message, a video, a computer program, or any wide variety of other kinds of data. Certain files can store multiple data types at once. By using computer programs, a person can open, read, change, save, and close a computer file. Computer files may be reopened, modified, and copied an arbitrary number of times. Files are typically organized in a file system, which tracks file locations on the disk and enables user access. Etymology The word "file" derives from the Latin ''filum'' ("a thread"). "File" was used in the conte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decrypt
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan horses, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
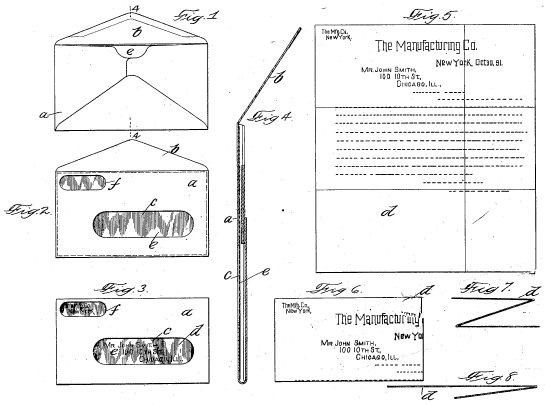
Envelope
An envelope is a common packaging item, usually made of thin, flat material. It is designed to contain a flat object, such as a letter or card. Traditional envelopes are made from sheets of paper cut to one of three shapes: a rhombus, a short-arm cross or a kite. These shapes allow the envelope structure to be made by folding the sheet sides around a central rectangular area. In this manner, a rectangle-faced enclosure is formed with an arrangement of four flaps on the reverse side. Overview A folding sequence such that the last flap closed is on a short side is referred to in commercial envelope manufacture as a pocket – a format frequently employed in the packaging of small quantities of seeds. Although in principle the flaps can be held in place by securing the topmost flap at a single point (for example with a wax seal), generally they are pasted or gummed together at the overlaps. They are most commonly used for enclosing and sending mail (letters) through a prepaid- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Corruption
In the pursuit of knowledge, data (; ) is a collection of discrete values that convey information, describing quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted. A datum is an individual value in a collection of data. Data is usually organized into structures such as tables that provide additional context and meaning, and which may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data is commonly used in scientific research, economics, and in virtually every other form of human organizational activity. Examples of data sets include price indices (such as consumer price index), unemployment rates, literacy rates, and census data. In this context, data represents the raw facts and figures which can be used in such a manner in order to capture the useful information out of it. Da ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |