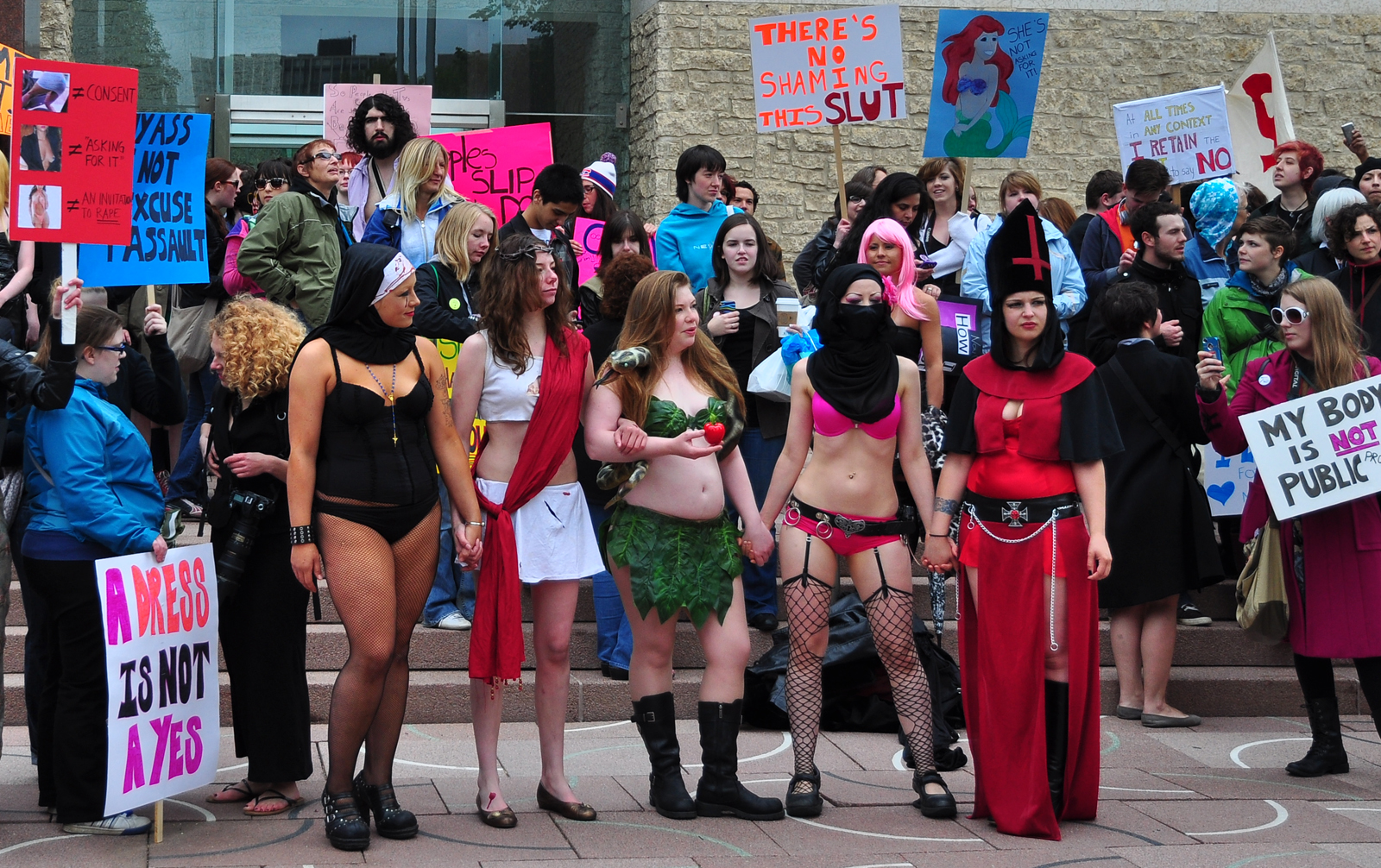|
Cyberbullying
Cyberbullying or cyberharassment is a form of bullying or harassment using electronic means. Cyberbullying and cyberharassment are also known as online bullying. It has become increasingly common, especially among teenagers, as the digital sphere has expanded and technology has advanced. Cyberbullying is when someone, typically a teenager, bullies or harasses others on the internet and other digital spaces, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims' personal information, or pejorative labels (i.e. hate speech). Bullying or harassment can be identified by repeated behavior and an intent to harm. Victims of cyberbullying may experience lower self-esteem, increased suicidal ideation, and various negative emotional responses, including being anxious, frustrated, angry, or depressed. Cyberbullying is in many cases an extension of already existing traditional bullying. Students who are bullied ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and military networks in the 1970s to enable resource shari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bureau Of Justice Statistics
The Bureau of Justice Statistics (BJS) of the U.S. Department of Justice is the principal federal agency responsible for measuring crime, criminal victimization, criminal offenders, victims of crime, correlates of crime, and the operation of criminal and civil justice systems at the federal, state, tribal, and local levels. Established on December 27, 1979, BJS collects, analyzes, and publishes data relating to crime in the United States. The agency publishes data regarding statistics gathered from the roughly fifty-thousand agencies, offices, courts, and institutions that together comprise the U.S. justice system. The mission of BJS is "To collect, analyze, publish, and disseminate information on crime, criminal offenders, victims of crime, and the operation of justice systems at all levels of government." BJS, along with the National Institute of Justice (NIJ), Bureau of Justice Assistance (BJA), Office of Juvenile Justice and Delinquency Prevention (OJJDP), Office for Victim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pornography
Pornography (often shortened to porn or porno) is the portrayal of sexual subject matter for the exclusive purpose of sexual arousal. Primarily intended for adults,"Kids Need Porn Literacy" – , ''Psychology Today'', 30 October 2016 pornography is presented in a variety of media, including , , |
Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
False Victimization
Victim blaming occurs when the victim of a crime or any wrongful act is held entirely or partially at fault for the harm that befell them. There is historical and current prejudice against the victims of domestic violence and sex crimes, such as the greater tendency to blame victims of rape than victims of robbery if victims and perpetrators knew each other prior to the commission of the crime. Coining of the phrase Psychologist William Ryan coined the phrase "blaming the victim" in his 1971 book of that title. In the book, Ryan described victim blaming as an ideology used to justify racism and social injustice against black people in the United States. Ryan wrote the book to refute Daniel Patrick Moynihan's 1965 work ''The Negro Family: The Case for National Action'' (usually simply referred to as the Moynihan Report). Moynihan had concluded that three centuries of oppression of black people, and in particular with what he calls the uniquely cruel structure of American slavery ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface identification and location addressing. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s. IP addresses are written and displayed in human-readable notations, such as in IPv4, and in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., , which is equivalent to the historically used subnet mask . The IP address space is managed globally by the Internet Assigned Numbers Authority (IA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Amazon
Amazon most often refers to: * Amazons, a tribe of female warriors in Greek mythology * Amazon rainforest, a rainforest covering most of the Amazon basin * Amazon River, in South America * Amazon (company), an American multinational technology company Amazon or Amazone may also refer to: Places South America * Amazon Basin (sedimentary basin), a sedimentary basin at the middle and lower course of the river * Amazon basin, the part of South America drained by the river and its tributaries * Amazon Reef, at the mouth of the Amazon basin Elsewhere * 1042 Amazone, an asteroid * Amazon Creek, a stream in Oregon, US People * Amazon Eve (born 1979), American model, fitness trainer, and actress * Lesa Lewis (born 1967), American professional bodybuilder nicknamed "Amazon" Art and entertainment Fictional characters * Amazon (Amalgam Comics) * Amazon, an alias of the Marvel supervillain Man-Killer * Amazons (DC Comics), a group of superhuman characters * The Amazon, a ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
False Accusations
A false accusation is a claim or allegation of wrongdoing that is untrue and/or otherwise unsupported by facts. False accusations are also known as groundless accusations or unfounded accusations or false allegations or false claims. They can occur in any of the following contexts: * Informally in everyday life * Quasi-judicially * Judicially Types When there is insufficient supporting evidence to determine whether it is true or false, an accusation is described as "unsubstantiated" or "unfounded". Accusations that are determined to be false based on corroborating evidence can be divided into three categories: * A completely false allegation, in that the alleged events did not occur. * An allegation that describes events that did occur, but were perpetrated by an individual who is not accused, and in which the accused person is innocent. * An allegation that is false, in that it mixes descriptions of events that actually happened with other events that did not occur. A false allega ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Threats
A threat is a communication of intent to inflict harm or loss on another person. Intimidation is a tactic used between conflicting parties to make the other timid or psychologically insecure for coercion or control. The act of intimidation for coercion is considered as a threat. Threatening or threatening behavior (or criminal threatening behavior) is the crime of intentionally or knowingly putting another person in fear of bodily injury. "Threat of harm generally involves a perception of injury...physical or mental damage...act or instance of injury, or a material and detriment or loss to a person." Some of the more common types of threats forbidden by law are those made with an intent to obtain a monetary advantage or to compel a person to act against their will. In most US states, it is an offense to threaten to (1) use a deadly weapon on another person; (2) injure another's person or property; or (3) injure another's reputation. Law Brazil In Brazil, the crime of threateni ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Feud
A feud , referred to in more extreme cases as a blood feud, vendetta, faida, clan war, gang war, or private war, is a long-running argument or fight, often between social groups of people, especially families or clans. Feuds begin because one party perceives itself to have been attacked, insulted, injured, or otherwise wronged by another. Intense feelings of resentment trigger an initial retribution, which causes the other party to feel greatly aggrieved and vengeful. The dispute is subsequently fuelled by a long-running cycle of retaliatory violence. This continual cycle of provocation and retaliation usually makes it extremely difficult to end the feud peacefully. Feuds can persist for generations and may result in extreme acts of violence. They can be interpreted as an extreme outgrowth of social relations based in family honor. Until the early modern period, feuds were considered legitimate legal instruments and were regulated to some degree. For example, Montenegrin cultur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |