|
Constant Weight Code
In coding theory, a constant-weight code, also called an ''m''-of-''n'' code, is an error detection and correction code where all codewords share the same Hamming weight. The one-hot code and the balanced code are two widely used kinds of constant-weight code. The theory is closely connected to that of designs (such as ''t''-designs and Steiner systems). Most of the work on this field of discrete mathematics is concerned with ''binary'' constant-weight codes. Binary constant-weight codes have several applications, including frequency hopping in GSM networks.D. H. Smith, L. A. Hughes and S. Perkins (2006).A New Table of Constant Weight Codes of Length Greater than 28. ''The Electronic Journal of Combinatorics'' 13. Most barcodes use a binary constant-weight code to simplify automatically setting the brightness threshold that distinguishes black and white stripes. Most line codes use either a constant-weight code, or a nearly-constant-weight paired disparity code. In addi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
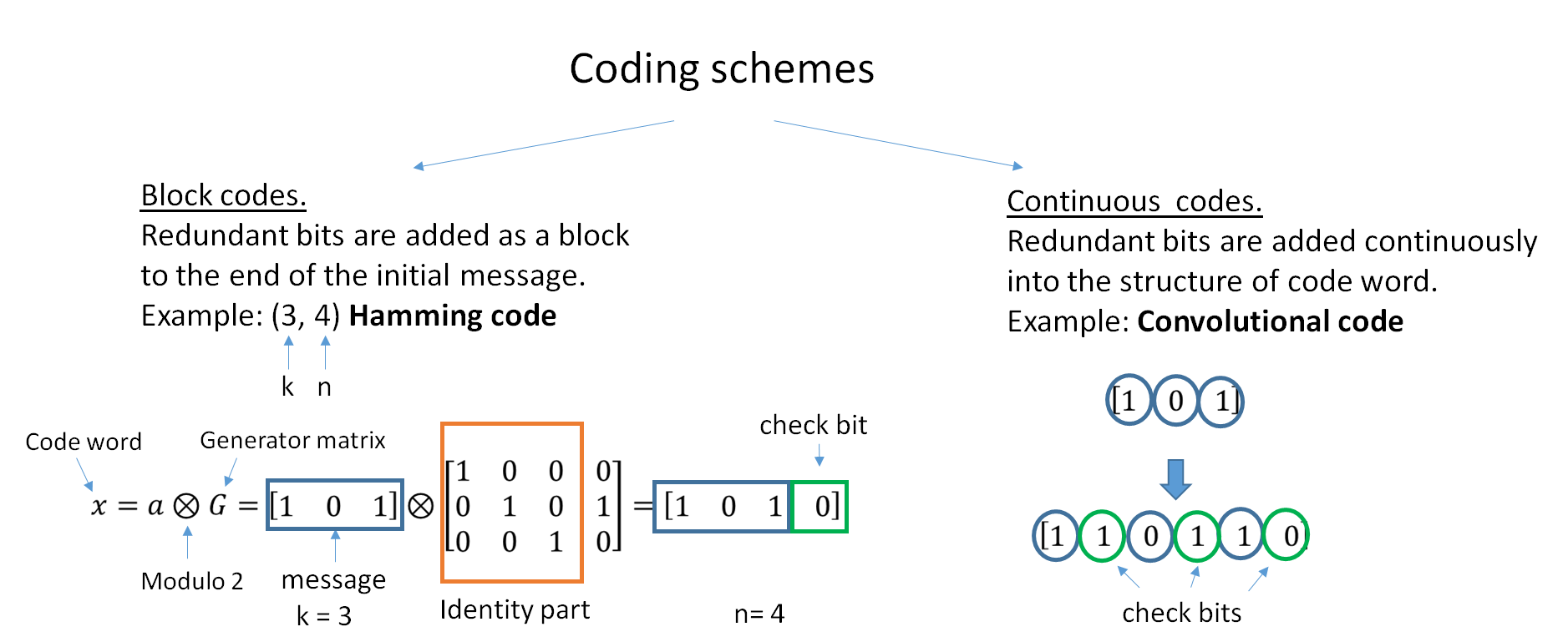
Coding Theory
Coding theory is the study of the properties of codes and their respective fitness for specific applications. Codes are used for data compression, cryptography, error detection and correction, data transmission and data storage. Codes are studied by various scientific disciplines—such as information theory, electrical engineering, mathematics, linguistics, and computer science—for the purpose of designing efficient and reliable data transmission methods. This typically involves the removal of redundancy and the correction or detection of errors in the transmitted data. There are four types of coding: # Data compression (or ''source coding'') # Error control (or ''channel coding'') # Cryptographic coding # Line coding Data compression attempts to remove unwanted redundancy from the data from a source in order to transmit it more efficiently. For example, ZIP data compression makes data files smaller, for purposes such as to reduce Internet traffic. Data compression a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
First Johnson Bound
In applied mathematics, the Johnson bound (named after Selmer Martin Johnson) is a limit on the size of error-correcting codes, as used in coding theory for data transmission or communications. Definition Let C be a ''q''-ary code of length n, i.e. a subset of \mathbb_q^n. Let d be the minimum distance of C, i.e. :d = \min_ d(x,y), where d(x,y) is the Hamming distance between x and y. Let C_q(n,d) be the set of all ''q''-ary codes with length n and minimum distance d and let C_q(n,d,w) denote the set of codes in C_q(n,d) such that every element has exactly w nonzero entries. Denote by , C, the number of elements in C. Then, we define A_q(n,d) to be the largest size of a code with length n and minimum distance d: : A_q(n,d) = \max_ , C, . Similarly, we define A_q(n,d,w) to be the largest size of a code in C_q(n,d,w): : A_q(n,d,w) = \max_ , C, . Theorem 1 (Johnson bound for A_q(n,d)): If d=2t+1, : A_q(n,d) \leq \frac. If d=2t+2, : A_q(n,d) \leq \frac. Theorem 2 (John ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hadamard Code
The Hadamard code is an error-correcting code named after Jacques Hadamard that is used for error detection and correction when transmitting messages over very noisy or unreliable channels. In 1971, the code was used to transmit photos of Mars back to Earth from the NASA space probe Mariner 9. Because of its unique mathematical properties, the Hadamard code is not only used by engineers, but also intensely studied in coding theory, mathematics, and theoretical computer science. The Hadamard code is also known under the names Walsh code, Walsh family, and Walsh–Hadamard code in recognition of the American mathematician Joseph Leonard Walsh. The Hadamard code is an example of a linear code of length 2^m over a binary alphabet. Unfortunately, this term is somewhat ambiguous as some references assume a message length k = m while others assume a message length of k = m+1. In this article, the first case is called the Hadamard code while the second is called the augmented Hadamar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
6b/8b Encoding
In telecommunications, 6b/8b is a line code that expands 6-bit codes to 8-bit symbols for the purposes of maintaining DC-balance in a communications system. The 6b/8b encoding is a balanced code -- each 8-bit output symbol contains 4 zero bits and 4 one bits. So the code can, like a parity bit, detect all single-bit errors. The number of 8-bit patterns with 4 bits set is the binomial coefficient \tbinom 84 = 70. Further excluding the patterns 11110000 and 00001111, this allows 68 coded patterns: 64 data codes, plus 4 additional control codes. Coding rules The 64 possible 6-bit input codes can be classified according to their disparity, the number of 1 bits minus the number of 0 bits: The 6-bit input codes are mapped to 8-bit output symbols as follows: * The 20 6-bit codes with disparity 0 are prefixed with 10''Example: 000111 → 10000111''''Example: 101010 → 10101010'' * The 15 6-bit codes with disparity +2, other than 001111, are prefixed with 00''Example: 010111 → 0001 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kees Schouhamer Immink
Kornelis Antonie "Kees" Schouhamer Immink (born 18 December 1946) is a Dutch scientist, inventor, and entrepreneur, who pioneered and advanced the era of digital audio, video, and data recording, including popular digital media such as Compact Disc, DVD and Blu-ray Disc.National Academy of Engineering He has been a prolific and influential engineer, who holds more than 1100 U.S. and international patents. A large portion of the commonly used audio and video playback and recording devices use technologies based on his work. His contributions to coding systems assisted the digital video and audio revolution, by enabling reliable data storage at information densities previously unattainable. Immink rec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unidirectional Error
In telecommunication, a Berger code is a unidirectional error detecting code, named after its inventor, J. M. Berger. Berger codes can detect all unidirectional errors. Unidirectional errors are errors that only flip ones into zeroes or only zeroes into ones, such as in asymmetric channels. The check bits of Berger codes are computed by counting all the zeroes in the information word, and expressing that number in natural binary. If the information word consists of n bits, then the Berger code needs k = \lceil \log_2 (n+1)\rceil "check bits", giving a Berger code of length k+n. (In other words, the k check bits are enough to check up to n = 2^k - 1 information bits). Berger codes can detect any number of one-to-zero bit-flip errors, as long as no zero-to-one errors occurred in the same code word. Similarly, Berger codes can detect any number of zero-to-one bit-flip errors, as long as no one-to-zero bit-flip errors occur in the same code word. Berger codes cannot correct any error. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Donald Knuth
Donald Ervin Knuth ( ; born January 10, 1938) is an American computer scientist, mathematician, and professor emeritus at Stanford University. He is the 1974 recipient of the ACM Turing Award, informally considered the Nobel Prize of computer science. Knuth has been called the "father of the analysis of algorithms". He is the author of the multi-volume work ''The Art of Computer Programming'' and contributed to the development of the rigorous analysis of the computational complexity of algorithms and systematized formal mathematical techniques for it. In the process, he also popularized the asymptotic notation. In addition to fundamental contributions in several branches of theoretical computer science, Knuth is the creator of the TeX computer typesetting system, the related METAFONT font definition language and rendering system, and the Computer Modern family of typefaces. As a writer and scholar, Knuth created the WEB and CWEB computer programming systems designed to encou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forward Error Correction
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is the sender encodes the message with redundant information in the form of an ECC. The redundancy allows the receiver to detect a limited number of errors that may occur anywhere in the message, and often to correct these errors without retransmission. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. ECC contrasts with error detection in that errors that are encountered can be corrected, not simply detected. The advantage is that a system using ECC does not require a reverse channel to request retransmission of data when an error occurs. The downside is that there is a fixed overhead that is added to the message, thereby requiring a h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Binary Numeral System
A binary number is a number expressed in the base-2 numeral system or binary numeral system, a method of mathematical expression which uses only two symbols: typically "0" (zero) and "1" ( one). The base-2 numeral system is a positional notation with a radix of 2. Each digit is referred to as a bit, or binary digit. Because of its straightforward implementation in digital electronic circuitry using logic gates, the binary system is used by almost all modern computers and computer-based devices, as a preferred system of use, over various other human techniques of communication, because of the simplicity of the language and the noise immunity in physical implementation. History The modern binary number system was studied in Europe in the 16th and 17th centuries by Thomas Harriot, Juan Caramuel y Lobkowitz, and Gottfried Leibniz. However, systems related to binary numbers have appeared earlier in multiple cultures including ancient Egypt, China, and India. Leibniz was specifica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Address Decoder
In digital electronics, an address decoder is a binary decoder that has two or more inputs for address bits and one or more outputs for device selection signals. When the address for a particular device appears on the address inputs, the decoder asserts the selection output for that device. A dedicated, single-output address decoder may be incorporated into each device on an address bus, or a single address decoder may serve multiple devices. A single address decoder with n address input bits can serve up to 2n devices. Several members of the 7400 series of integrated circuits can be used as address decoders. For example, when used as an address decoder, the 74154 provides four address inputs and sixteen (i.e., 24) device selector outputs. An address decoder is a particular use of a binary decoder circuit known as a "demultiplexer" or "demux" (the 74154 is commonly called a "4-to-16 demultiplexer"), which has many other uses besides address decoding. Address decoders are fundamenta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pulse-position Modulation
Pulse-position modulation (PPM) is a form of signal modulation in which ''M'' message bits are encoded by transmitting a single pulse in one of 2^M possible required time shifts. This is repeated every ''T'' seconds, such that the transmitted bit rate is M/T bits per second. It is primarily useful for optical communications systems, which tend to have little or no multipath interference. History An ancient use of pulse-position modulation was the Greek hydraulic semaphore system invented by Aeneas Stymphalus around 350 B.C. that used the water clock principle to time signals. In this system, the draining of water acts as the timing device, and torches are used to signal the pulses. The system used identical water-filled containers whose drain could be turned on and off, and a float with a rod marked with various predetermined codes that represented military messages. The operators would place the containers on hills so they could be seen from each other at a distance. To send a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |