|
Client Honeypot
Honeypots are security devices whose value lie in being probed and compromised. Traditional honeypots are servers (or devices that expose server services) that wait passively to be attacked. Client Honeypots are active security devices in search of malicious servers that attack clients. The client honeypot poses as a client and interacts with the server to examine whether an attack has occurred. Often the focus of client honeypots is on web browsers, but any client that interacts with servers can be part of a client honeypot (for example ftp, ssh, email, etc.). There are several terms that are used to describe client honeypots. Besides client honeypot, which is the generic classification, honeyclient is the other term that is generally used and accepted. However, there is a subtlety here, as "honeyclient" is actually a homograph that could also refer to the first known open source client honeypot implementation (see below), although this should be clear from the context. Architect ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Honeypot (computing)
In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site which contains information or resources of value to attackers. It is actually isolated, monitored, and capable of blocking or analyzing the attackers. This is similar to police sting operations, colloquially known as "baiting" a suspect. Types Honeypots can be classified based on their deployment (use/action) and based on their level of involvement. Based on deployment, honeypots may be classified as: * production honeypots * research honeypots Production honeypots are easy to use, capture only limited information, and are used primarily by corporations. Production honeypots are placed inside the production network with other production servers by an organization to improve their overa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
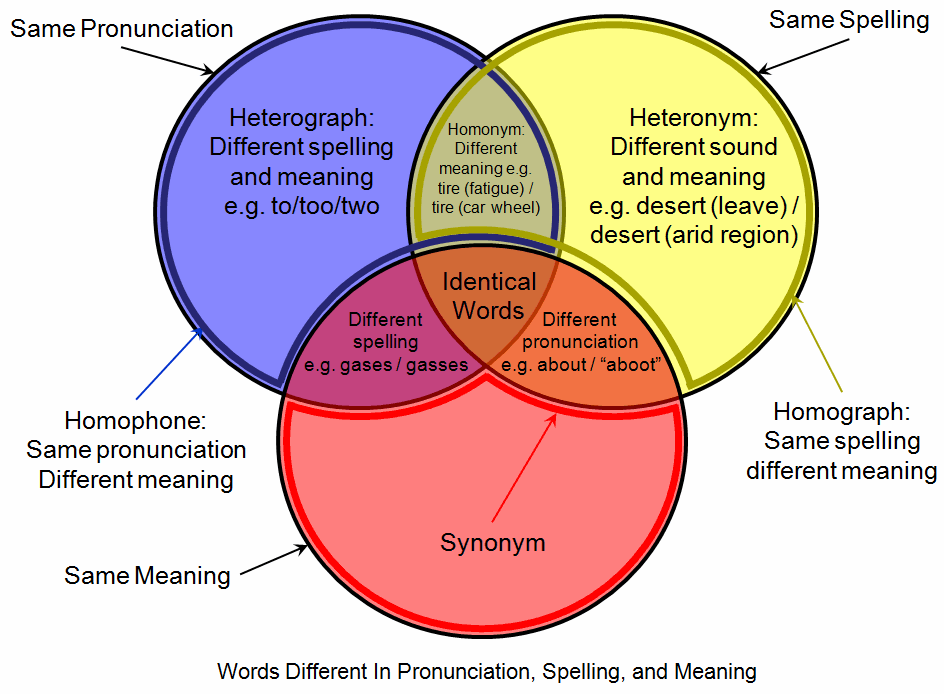
Homograph
A homograph (from the el, ὁμός, ''homós'', "same" and γράφω, ''gráphō'', "write") is a word that shares the same written form as another word but has a different meaning. However, some dictionaries insist that the words must also be pronounced differently, while the Oxford English Dictionary says that the words should also be of "different origin". In this vein, ''The Oxford Guide to Practical Lexicography'' lists various types of homographs, including those in which the words are discriminated by being in a different ''word class'', such as ''hit'', the verb ''to strike'', and ''hit'', the noun ''a blow''. If, when spoken, the meanings may be distinguished by different pronunciations, the words are also heteronyms. Words with the same writing ''and'' pronunciation (i.e. are both homographs and homophones) are considered homonyms. However, in a looser sense the term "homonym" may be applied to words with the same writing ''or'' pronunciation. Homograph disambiguat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Logic Bomb
A logic bomb is a piece of code intentionally inserted into a software system that will set off a malicious function when specified conditions are met. For example, a programmer may hide a piece of code that starts deleting files (such as a salary database trigger), should they ever be terminated from the company. Software that is inherently malicious, such as viruses and worms, often contain logic bombs that execute a certain payload at a pre-defined time or when some other condition is met. This technique can be used by a virus or worm to gain momentum and spread before being noticed. Some viruses attack their host systems on specific dates, such as Friday the 13th or April Fools' Day. Trojans and other computer viruses that activate on certain dates are often called " time bombs". To be considered a logic bomb, the payload should be unwanted and unknown to the user of the software. As an example, trial programs with code that disables certain functionality after a set ti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MITRE
The mitre (Commonwealth English) (; Greek: μίτρα, "headband" or "turban") or miter (American English; see spelling differences), is a type of headgear now known as the traditional, ceremonial headdress of bishops and certain abbots in traditional Christianity. Mitres are worn in the Catholic Church, Eastern Orthodox Church, Oriental Orthodox Churches, the Anglican Communion, some Lutheran churches, for important ceremonies, by the Metropolitan of the Malankara Mar Thoma Syrian Church, and also, in the Catholic Church, all cardinals, whether or not bishops, and some Eastern Orthodox archpriests. Etymology μίτρα, ''mítra'' ( Ionic μίτρη, ''mítrē'') is Greek, and means a piece of armour, usually a metal guard worn around the waist and under a cuirass, as mentioned in Homer's Iliad. In later poems, it was used to refer to a headband used by women for their hair; and a sort of formal Babylonian headdress, as mentioned by Herodotus (''Histories'' 1.195 and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Niels Provos
Niels Provos is a German-American researcher in security engineering, malware, and cryptography. He received a PhD in computer science from the University of Michigan. From 2003 to 2018, he worked at Google as a Distinguished Engineer on security for Google Cloud Platform. In 2018, he left Google to join Stripe as its new head of security. For many years, Provos contributed to the OpenBSD operating system, where he developed the bcrypt adaptive cryptographic hash function. He is the author of numerous software packages, including the libevent event driven programming system, the Systrace access control system, the honeyd honeypot system, the StegDetect steganography detector, the Bcrypt password encryption technique, and many others. Provos has been an outspoken critic of the effect of the DMCA and similar laws on security researchers, arguing that they threaten to make criminals of people conducting legitimate security research. Provos has also served as the Program Chair of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CERT Polska
CERT Polska is Computer Emergency Response Team which operates within the structures of Naukowa i Akademicka Sieć Komputerowa (Scientific and Academic Computer Network or NASK) – a research institute which conducts scientific activity, operates the national .pl domain registry and provides advanced IT network services. CERT Polska is the first Polish computer emergency response team. Active since 1996 in the environment of response teams, it became a recognised and experienced entity in the field of computer security. Since its launch, the core of the team's activity has been handling security incidents and cooperation with similar units worldwide. It also conducts extensive R&D into security topics. In 1997, CERT Polska became a member of the international forum of response teams – FIRST, and since 2000 it has been a member of the working group of European response teams – TERENA TF-CSIRT and an associated organisation Trusted Introducer. In 2005 on the initiative of CERT Pol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SURFnet
SURF is an organization that develops, implements and maintains the national research and education network (NREN) of the Netherlands, It operates the national research network formally called SURFnet. SURF as a network is a backbone computer network reserved for higher education and research in the Netherlands. SURF is a cooperative association of Dutch educational and research institutions in which the members combine their strengths. They work together to acquire or develop digital services and to encourage knowledge sharing through continuous innovation. The members are the owners of SURF. History The organization was established in 1986, it started supplying IP connectivity services in 1989, deploying the TCP/IP suite. SURFnet has deployed a series of network generations in an overbuilt manner. The initial SURFnet network was based on 9.6 kbit/s and 64 kbit/s X.25 connections, providing DECNET protocol. SURFnet2 was established in 1989 and delivered TCP/IP over an X.25 netw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Internet Society
The Internet Society (ISOC) is an American nonprofit advocacy organization founded in 1992 with local chapters around the world. Its mission is "to promote the open development, evolution, and use of the Internet for the benefit of all people throughout the world." It has offices in Reston, Virginia, U.S., and Geneva, Switzerland. Organization The Internet Society has regional bureaus worldwide, composed of chapters, organizational members, and, as of July 2020, more than 70,000 individual members. The Internet Society has a staff of more than 100 and was governed by a board of trustees, whose members are appointed or elected by the society's chapters, organization members, and the Internet Engineering Task Force (IETF). The IETF comprised the Internet Society's volunteer base. Its leadership includes Chairman of the Board of Trustees, Ted Hardie; and President and CEO, Andrew Sullivan. The Internet Society created the Public Interest Registry (PIR), launched the Internet Ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deborah Frincke
Deborah A. Frincke is an American academic and computer scientist specializing in computer security who is the associate laboratories director of national security programs at Sandia National Laboratories. Education Frincke was educated at the University of California, Davis, earning a Bachelor of Science degree in computer science and mathematics in 1985, a Master of Science in computer science in 1989, and a PhD in computer science in 1992. Career Frincke began her career as a professor of computer science at the University of Idaho. She is the former chief scientist for cyber security at the Pacific Northwest National Laboratory, one of the United States Department of Energy national laboratories. From 2014 to 2020, she was director of research for the National Security Agency. As Research Director, Frincke also served as the NSA Science Advisor and the NSA Innovation Champion. She also served as the NSA Science Advisor and the NSA Innovation Champion. Prior to becoming ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Waikato
, mottoeng = For The People , established = 1964; years ago , endowment = (31 December 2021) , budget = NZD $263.6 million (31 December 2020) , chancellor = Sir Anand Satyanand, GNZM, QSO, KStJ , vice_chancellor = Neil Quigley , city = Hamilton , province = Waikato , country = New Zealand (Māori: ''Kirikiriroa, Waikato, Aotearoa'') , administrative_staff = 1,499 (FTS, 2020) , students = 10,448 (EFTS, 2020) , type = Public research university , campus = Suburban 65 ha (160 acres) , colours = UW Red, Gold and Black , affiliations = ACU, ASAIHL, AACSB, AMBA, EQUIS , website Waikato.ac.nz, logo = The University of Waikato ( mi, Te Whare Wānanga o Waikato), is a public research university in Hamilton, New Zealand established in 1964. An additional campus is located in Tauranga. The university performs research in the disciplines of education, social sciences, and management and is an innovator in environmental science, marine and freshwater ecolo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |