|
Churning (cipher)
Churning is an encryption function used to scramble downstream user data of the ATM passive optical network system defined by the ITU G.983.1 standard. The standard states that churning "offers a low level of protection for data confidentiality". Cryptanalysis had shown that "the churning cipher is robustly weak". Algorithm Churning uses 24 bits of the key, designated X1..X8 and P1..P16. Ten static K bits are generated from the key: K1 = (X1×P13×P14) + (X2×P13×not P14) + (X7×not P13×P14) + (X8×not P13×not P14) K2 = (X3×P15×P16) + (X4×P15×not P16) + (X5×not P15×P16) + (X6×not P15×not P16) K3 = (K1×P9) + (K2×not P9) K4 = (K1×not P9) + (K2×P9) K5 = (K1×P10) + (K2×not P10) K6 = (K1×not P10) + (K2×P10) K7 = (K1×P11) + (K2×not P11) K8 = (K1×not P11) + (K2×P11) K9 = (K1×P12) + (K2×not P12) K10 = (K1×not P12) + (K2×P12) The churning transforms eight bits into eight bits: (Z1..Z4) = TransformNibble(Y1..Y4, K1, P1, K3, K2, P2, K4, K1, K3, K5, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asynchronous Transfer Mode
Asynchronous Transfer Mode (ATM) is a telecommunications standard defined by American National Standards Institute (ANSI) and ITU-T (formerly CCITT) for digital transmission of multiple types of traffic. ATM was developed to meet the needs of the Broadband Integrated Services Digital Network as defined in the late 1980s, and designed to integrate telecommunication networks. It can handle both traditional high-throughput data traffic and real-time, low-latency content such as telephony (voice) and video.ATM Forum, The User Network Interface (UNI), v. 3.1, , Prentice Hall PTR, 1995, page 2. ATM provides functionality that uses features of circuit switching and packet switching networks by using asynchronous time-division multiplexing.McDysan (1999), p. 287. In the OSI reference model data link layer (layer 2), the basic transfer units are called '' frames''. In ATM these frames are of a fixed length (53 octets) called ''cells''. This differs from approaches such as Internet Pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
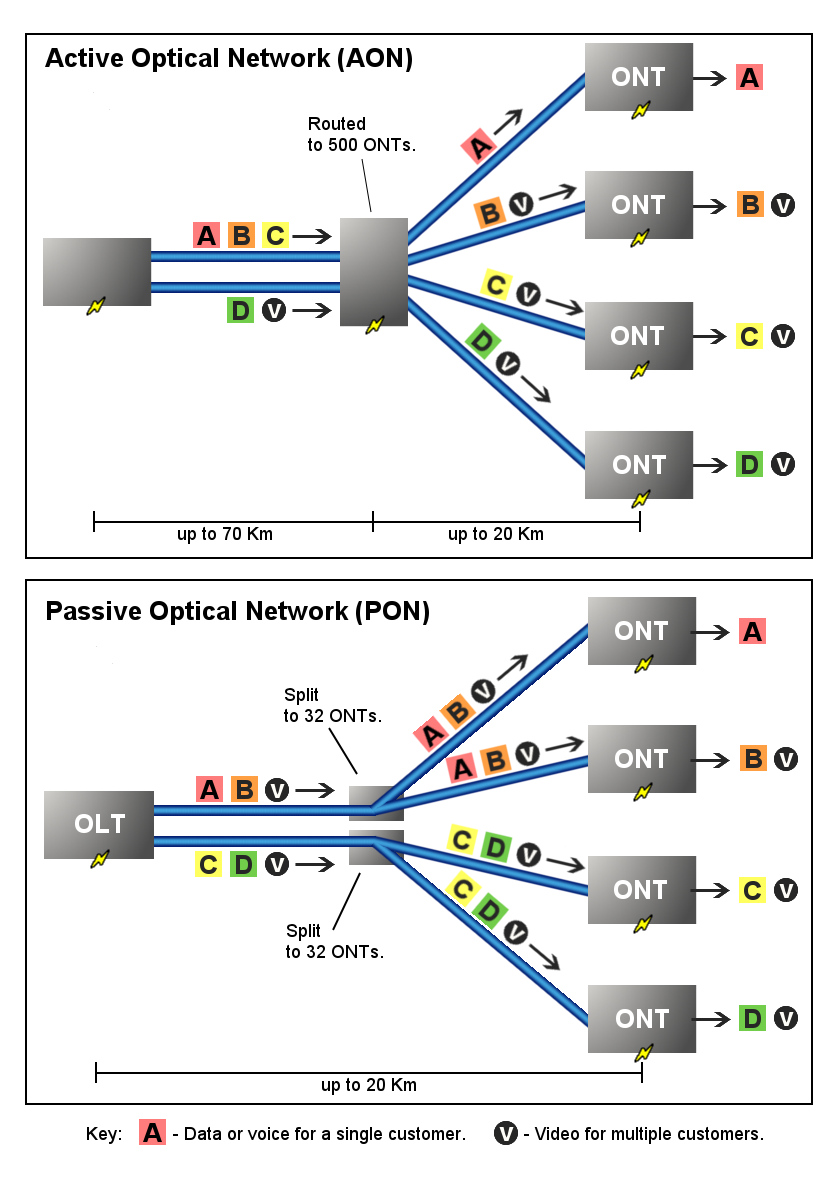
Passive Optical Network
A passive optical network (PON) is a fiber-optic telecommunications technology for delivering broadband network access to end-customers. Its architecture implements a point-to-multipoint topology in which a single optical fiber serves multiple endpoints by using unpowered (''passive'') fiber optic splitters to divide the fiber bandwidth among the endpoints. Passive optical networks are often referred to as the '' last mile'' between an Internet service provider (ISP) and its customers. Components and characteristics A passive optical network consists of an optical line terminal (OLT) at the service provider's central office (hub) and a number of optical network units (ONUs) or optical network terminals (ONTs), near end users. A PON reduces the amount of fiber and central office equipment required compared with point-to-point architectures. A passive optical network is a form of fiber-optic access network. In most cases, downstream signals are broadcast to all premises sharing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Substitution Cipher
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with the help of a key; the "units" may be single letters (the most common), pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing the inverse substitution process to extract the original message. Substitution ciphers can be compared with transposition ciphers. In a transposition cipher, the units of the plaintext are rearranged in a different and usually quite complex order, but the units themselves are left unchanged. By contrast, in a substitution cipher, the units of the plaintext are retained in the same sequence in the ciphertext, but the units themselves are altered. There are a number of different types of substitution cipher. If the cipher operates on single letters, it is termed a simple substitution cipher; a cipher that operates on larger groups of letters ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PMC Sierra
PMC-Sierra was a global fabless semiconductor company with offices worldwide that developed and sold semiconductor devices into the storage, communications, optical networking, printing, and embedded computing marketplaces. On January 15, 2016, Microsemi Corporation completed acquisition of PMC-Sierra through Microsemi's subsidiary Lois Acquisition. History Sierra Semiconductor was founded in 1984 in San Jose, California by James Diller. It received funding on January 11, 1984 from Sequoia Capital, and went public in 1991. Pacific Microelectronics Centre (PMC) in Burnaby, British Columbia, Canada, was spun off from Microtel Pacific Research (the research arm of BC TEL at the time) to develop Asynchronous Transfer Mode (ATM) and later SONET integrated circuits (chips). With investment from Sierra Semiconductor, PMC was established in 1992 as a private company focused on providing networking semiconductors, and became a wholly owned, independently operated subsidiary of Sierra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |