|
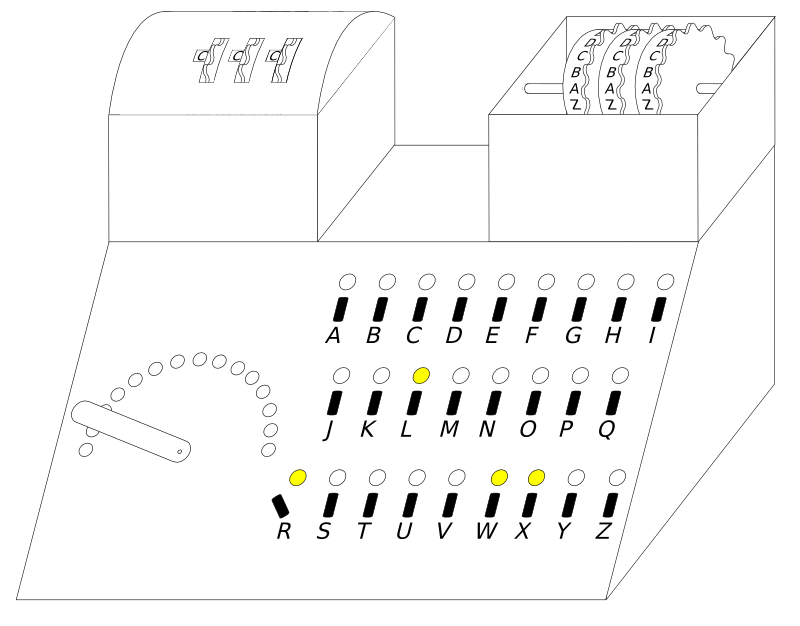
Card Catalog (cryptology)
The card catalog, or "catalog of characteristics," in cryptography, was a system designed by Polish Cipher Bureau mathematician-cryptologist Marian Rejewski, and first completed about 1935 or 1936, to facilitate decrypting German Enigma ciphers. History The Polish Cipher Bureau used the theory of permutations to start breaking the Enigma cipher in late 1932. The Bureau recognized that the Enigma machine's doubled-key (see Grill (cryptology)) permutations formed cycles, and those cycles could be used to break the cipher. With German cipher keys provided by a French spy, the Bureau was able to reverse engineer the Enigma and start reading German messages. At the time, the Germans were using only 6 ''steckers'', and the Polish grill method was feasible. On 1 August 1936, the Germans started using 8 ''steckers'', and that change made the grill method less feasible. The Bureau needed an improved method to break the German cipher. Although the ''steckers'' would change which letter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyclometer
The cyclometer was a cryptologic device designed, "probably in 1934 or 1935," by Marian Rejewski of the Polish Cipher Bureau's German section (BS-4) to facilitate decryption of German Enigma ciphertext. The original machines are believed to have been destroyed shortly before the German invasion of Poland that launched the Second World War, to prevent the Germans learning that their cipher had been broken. Using drawings made by Rejewski, Hal Evans and Tim Flack at the Department of Engineering, University of Cambridge, in 2019 constructed a working version of the cyclometer. History Example message Frode Weierud provides the procedure, secret settings, and results that were used in a 1930 German technical manual. Daily key (shared secret): Wheel Order : II I III Ringstellung : 24 13 22 (XMV) Reflector : A Plugboard : A-M, F-I, N-V, P-S, T-U, W-Z Grundstellung: FOL Operator chosen message key : ABL Enciphered starting with FOL: PKPJXI Cleartext m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
History Of Cryptography
Cryptography, the use of codes and ciphers to protect secrets, began thousands of years ago. Until recent decades, it has been the story of what might be called classical cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper. The development of cryptography has been paralleled by the development of cryptanalysis — the "breaking" of codes and ciphers. The discovery and application, early on, of frequency analysis to the reading of encrypted communications has, on occasion, altered the course of history. Thus the Zimmermann Telegram triggered the United States' en ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Christopher Kasparek
Christopher Kasparek (born 1945) is a Scottish-born writer of Polish descent who has translated works by numerous authors, including Ignacy Krasicki, Bolesław Prus, Florian Znaniecki, Władysław Tatarkiewicz, Marian Rejewski, and Władysław Kozaczuk, as well as the Polish–Lithuanian Constitution of 3 May 1791. He has published papers on the history of the World War II era; Enigma decryption; Bolesław Prus and his novel ''Pharaoh''; the theory and practice of translation; logology (science of science); multiple independent discovery; psychiatric nosology; and electronic health records. Life Born in Edinburgh, Scotland, to Józef and Stanisława (SylviaAcknowledgements in [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Władysław Kozaczuk
Władysław Kozaczuk (23 December 1923 – 26 September 2003) was a Polish Army colonel and a military and intelligence historian. Life Born in the village of Babiki near Sokółka, Kozaczuk joined the army in 1944, during World War II, at Białystok. In 1945 he became a Polish Army second lieutenant, and spent the first 5 years of his service commanding operational units of the Internal Security Corps, fighting the Polish anticommunist underground and then the Ukrainian Insurgent Army. In 1950 he was transferred to the Internal Security Corps Staff in Warsaw. In 1954–55, following the Korean War, Kozaczuk carried out armistice-related duties in Korea. In 1955–58 he served in the Polish Ministry of Internal Affairs ('). In 1957–58 he saw duty with the International Control Commission in Vietnam. In 1958–69 he served in Polish military counter-intelligence (''Wojskowa Służba Wewnętrzna''). According to his family, he found conditions there uncongenial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Perforated Sheets
The method of Zygalski sheets was a cryptologic technique used by the Polish Cipher Bureau before and during World War II, and during the war also by British cryptologists at Bletchley Park, to decrypt messages enciphered on German Enigma machines. The Zygalski-sheet apparatus takes its name from Polish Cipher Bureau mathematician–cryptologist Henryk Zygalski, who invented it about October 1938. Method Zygalski's device comprised a set of 26 perforated sheets for each of the, initially, six possible sequences for inserting the three rotors into the Enigma machine's scrambler. Each sheet related to the starting position of the left (slowest-moving) rotor. The 26 × 26 matrix represented the 676 possible starting positions of the middle and right rotors and was duplicated horizontally and vertically: ''a–z, a–y''. The sheets were punched with holes in the positions that would allow a "female" to occur. Polish mathematician–cryptologist Marian Rejewski writes about how ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Henryk Zygalski
Henryk Zygalski (; 15 July 1908 – 30 August 1978) was a Polish mathematician and cryptologist who worked at breaking German Enigma ciphers before and during World War II. Life Zygalski was born on 15 July 1908 in Posen, German Empire (now Poznań, Poland). He was, from September 1932, a civilian cryptologist with the Polish General Staff's ''Biuro Szyfrów'' (Cipher Bureau), housed in the Saxon Palace in Warsaw. He worked there with fellow Poznań University alumni and Cipher Bureau cryptology-course graduates Marian Rejewski and Jerzy Różycki. Together they developed methods and equipment for breaking Enigma messages. In late 1938, in response to growing complexities in German encryption procedures, Zygalski designed the "perforated sheets," also known as "Zygalski sheets," a manual device for finding Enigma settings. This scheme, like the earlier "card catalog," was independent of the number of connections being used in the Enigma's plugboard, or commutator. After the war ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bomba (cryptography)
The ''bomba'', or ''bomba kryptologiczna'' (Polish for "bomb" or "cryptologic bomb"), was a special-purpose machine designed around October 1938 by Polish Cipher Bureau cryptologist Marian Rejewski to break German Enigma-machine ciphers. Etymology How the machine came to be called a "bomb" has been an object of fascination and speculation. One theory, most likely apocryphal, originated with Polish engineer and army officer Tadeusz Lisicki (who knew Rejewski and his colleague Henryk Zygalski in wartime Britain but was never associated with the Cipher Bureau). He claimed that Jerzy Różycki (the youngest of the three Enigma cryptologists, and who had died in a Mediterranean passenger-ship sinking in January 1942) named the "bomb" after an ice-cream dessert of that name. This story seems implausible, since Lisicki had not known Różycki. Rejewski himself stated that the device had been dubbed a "bomb" "for lack of a better idea". Perhaps the most credible explanation is given ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reflector (cipher Machine)
A reflector, in cryptology, is a component of some rotor cipher machines, such as the Enigma machine, that sends electrical impulses that have reached it from the machine's rotors, back in reverse order through those rotors. The reflector simplified using the same machine setup for encryption and decryption, but it creates a weakness in the encryption: with a reflector the encrypted version of a given letter can never be that letter itself. That limitation aided World War II code breakers in cracking Enigma encryption. The comparable WW II U.S. cipher machine, SIGABA In the history of cryptography, the ECM Mark II was a cipher machine used by the United States for message encryption from World War II until the 1950s. The machine was also known as the SIGABA or Converter M-134 by the Army, or CSP-888/889 by the ..., did not include a reflector. Other names The reflector is also known as the reversing drum or, from the German, the ''Umkehrwalze'' or ''UKW''. {{crypto-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Partition Number
In number theory, the partition function represents the number of possible partitions of a non-negative integer . For instance, because the integer 4 has the five partitions , , , , and . No closed-form expression for the partition function is known, but it has both asymptotic expansions that accurately approximate it and recurrence relations by which it can be calculated exactly. It grows as an exponential function of the square root of its argument. The multiplicative inverse of its generating function is the Euler function; by Euler's pentagonal number theorem this function is an alternating sum of pentagonal number powers of its argument. Srinivasa Ramanujan first discovered that the partition function has nontrivial patterns in modular arithmetic, now known as Ramanujan's congruences. For instance, whenever the decimal representation of ends in the digit 4 or 9, the number of partitions of will be divisible by 5. Definition and examples For a positive integer , is t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Poland
Poland, officially the Republic of Poland, is a country in Central Europe. It is divided into 16 administrative provinces called voivodeships, covering an area of . Poland has a population of over 38 million and is the fifth-most populous member state of the European Union. Warsaw is the nation's capital and largest metropolis. Other major cities include Kraków, Wrocław, Łódź, Poznań, Gdańsk, and Szczecin. Poland has a temperate transitional climate and its territory traverses the Central European Plain, extending from Baltic Sea in the north to Sudeten and Carpathian Mountains in the south. The longest Polish river is the Vistula, and Poland's highest point is Mount Rysy, situated in the Tatra mountain range of the Carpathians. The country is bordered by Lithuania and Russia to the northeast, Belarus and Ukraine to the east, Slovakia and the Czech Republic to the south, and Germany to the west. It also shares maritime boundaries with Denmark and Sweden. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Grill (cryptology)
The grill method ( pl, metoda rusztu), in cryptology, was a method used chiefly early on, before the advent of the cyclometer, by the mathematician-cryptologists of the Polish Cipher Bureau ('' Biuro Szyfrów'') in decrypting German Enigma machine ciphers. The Enigma rotor cipher machine changes plaintext characters into cipher text using a different permutation for each character, and so implements a polyalphabetic substitution cipher. Background The German navy started using Enigma machines in 1926; it was called ''Funkschlüssel C'' ("Radio cipher C"). By 15 July 1928, the German Army (''Reichswehr'') had introduced their own version of the Enigma—the ''Enigma G''; a revised ''Enigma I'' (with plugboard) appeared in June 1930. The Enigma I used by the German military in the 1930s was a 3-rotor machine. Initially, there were only three rotors labeled ''I'', ''II'', and ''III'', but they could be arranged in any order when placed in the machine. Rejewski identified the rot ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |