|
Call Gate (Intel)
A call gate is a mechanism in Intel's x86 architecture for changing the privilege level of a process when it executes a predefined function call using a CALL FAR instruction. Overview Call gates are intended to allow less privileged code to call code with a higher privilege level. This type of mechanism is essential in modern operating systems that employ memory protection since it allows user applications to use kernel (operating system), kernel functions and system calls in a way that can be controlled by the operating system. Call gates use a special selector value to reference a descriptor accessed via the Global Descriptor Table or the Local Descriptor Table, which contains the information needed for the call across privilege boundaries. This is similar to the mechanism used for interrupts. Usage Assuming a call gate has been set up already by the operating system kernel (operating system), kernel, code simply does a CALL FAR with the necessary segment selector (the offset ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
X86 Architecture
x86 (also known as 80x86 or the 8086 family) is a family of complex instruction set computer (CISC) instruction set architectures initially developed by Intel, based on the 8086 microprocessor and its 8-bit-external-bus variant, the 8088. The 8086 was introduced in 1978 as a fully 16-bit extension of 8-bit Intel's 8080 microprocessor, with memory segmentation as a solution for addressing more memory than can be covered by a plain 16-bit address. The term "x86" came into being because the names of several successors to Intel's 8086 processor end in "86", including the 80186, 80286, 80386 and 80486. Colloquially, their names were "186", "286", "386" and "486". The term is not synonymous with IBM PC compatibility, as this implies a multitude of other computer hardware. Embedded systems and general-purpose computers used x86 chips before the PC-compatible market started, some of them before the IBM PC (1981) debut. , most desktop and laptop computers sold are based o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Multics
Multics ("MULTiplexed Information and Computing Service") is an influential early time-sharing operating system based on the concept of a single-level memory.Dennis M. Ritchie, "The Evolution of the Unix Time-sharing System", Communications of the ACM, Vol. 17, 1984, pp. 365-375. It has been written that Multics "has influenced all modern operating systems since, from microcomputers to mainframes." Initial planning and development for Multics started in 1964, in Cambridge, Massachusetts. Originally it was a cooperative project led by MIT ( Project MAC with Fernando Corbató) along with General Electric and Bell Labs. It was developed on the GE 645 computer, which was specially designed for it; the first one was delivered to MIT in January 1967. GE offered their earlier 635 systems with the Dartmouth Time-Sharing System which they called "Mark I" and intended to offer the 645 with Multics as a larger successor. Bell withdrew from the project in 1969 as it became clear it would ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Microsoft Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sectors of the computing industry – Windows (unqualified) for a consumer or corporate workstation, Windows Server for a Server (computing), server and Windows IoT for an embedded system. Windows is sold as either a consumer retail product or licensed to Original equipment manufacturer, third-party hardware manufacturers who sell products Software bundles, bundled with Windows. The first version of Windows, Windows 1.0, was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). The name "Windows" is a reference to the windowing system in GUIs. The 1990 release of Windows 3.0 catapulted its market success and led to various other product families ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Worm
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer. Many worms are designed only to spread, and do not attempt to change the systems they pass thro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Exploit (computer Security)
An exploit is a method or piece of code that takes advantage of Vulnerability (computer security), vulnerabilities in software, Application software, applications, Computer network, networks, operating systems, or Computer hardware, hardware, typically for malicious purposes. The term "exploit" derives from the English verb "to exploit," meaning "to use something to one’s own advantage." Exploits are designed to identify flaws, bypass security measures, gain unauthorized access to systems, take control of systems, install malware, or data breach, steal sensitive data. While an exploit by itself may not be a malware, it serves as a vehicle for delivering malicious software by breaching security controls. Researchers estimate that malicious exploits cost the global economy over US$450 billion annually. In response to this threat, organizations are increasingly utilizing cyber threat intelligence to identify vulnerabilities and prevent hacks before they occur. Description Expl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Protection Ring
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). On most operating systems, Ring 0 is the level with the most privileges and interacts most directly with the physical hardware such as certain CPU functionality (e.g. the control registers) and I/O controllers. Special mechanisms are provide ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Trap (computing)
In digital computers, an interrupt (sometimes referred to as a trap) is a request for the processor to ''interrupt'' currently executing code (when permitted), so that the event can be processed in a timely manner. If the request is accepted, the processor will suspend its current activities, save its state, and execute a function called an ''interrupt handler'' (or an ''interrupt service routine'', ISR) to deal with the event. This interruption is often temporary, allowing the software to resume normal activities after the interrupt handler finishes, although the interrupt could instead indicate a fatal error. Interrupts are commonly used by hardware devices to indicate electronic or physical state changes that require time-sensitive attention. Interrupts are also commonly used to implement computer multitasking and system calls, especially in real-time computing. Systems that use interrupts in these ways are said to be interrupt-driven. History Hardware interrupts were ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Matt Pietrek
Matt Pietrek (born 1966) is an American spirits and drinks writer, publisher, and rum historian. His 2022 book, ''Modern Caribbean Rum'' won the Tales of the Cocktail Spirited Award for Best New Book on Drinks Culture, History, or Spirits.Tales of the Cocktail 2023 Spirited Award Winners. Pietrek writes regularly for his Rum WonkRum Wonk Pietrek's rum blog. and Cocktail Wonk Cocktail Wonk Pietrek's cocktail blog. web sites. With his wife, Carrie Smith, he operates Wonk Press LLC, [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Application Code
This glossary of computer science is a list of definitions of terms and concepts used in computer science, its sub-disciplines, and related fields, including terms relevant to software, data science, and . A B C D E F G H I J K L M N O P Q R ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
OS/2
OS/2 is a Proprietary software, proprietary computer operating system for x86 and PowerPC based personal computers. It was created and initially developed jointly by IBM and Microsoft, under the leadership of IBM software designer Ed Iacobucci, intended as a replacement for DOS. The first version was released in 1987. A feud between the two companies beginning in 1990 led to Microsoft’s leaving development solely to IBM, which continued development on its own. OS/2 Warp 4 in 1996 was the last major upgrade, after which IBM slowly halted the product as it failed to compete against Microsoft's Microsoft Windows, Windows; updated versions of OS/2 were released by IBM until 2001. The name stands for "Operating System/2", because it was introduced as part of the same generation change release as IBM's "IBM Personal System/2, Personal System/2 (PS/2)" line of second-generation PCs. OS/2 was intended as a protected mode, protected-mode successor of IBM PC DOS, PC DOS targeting t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
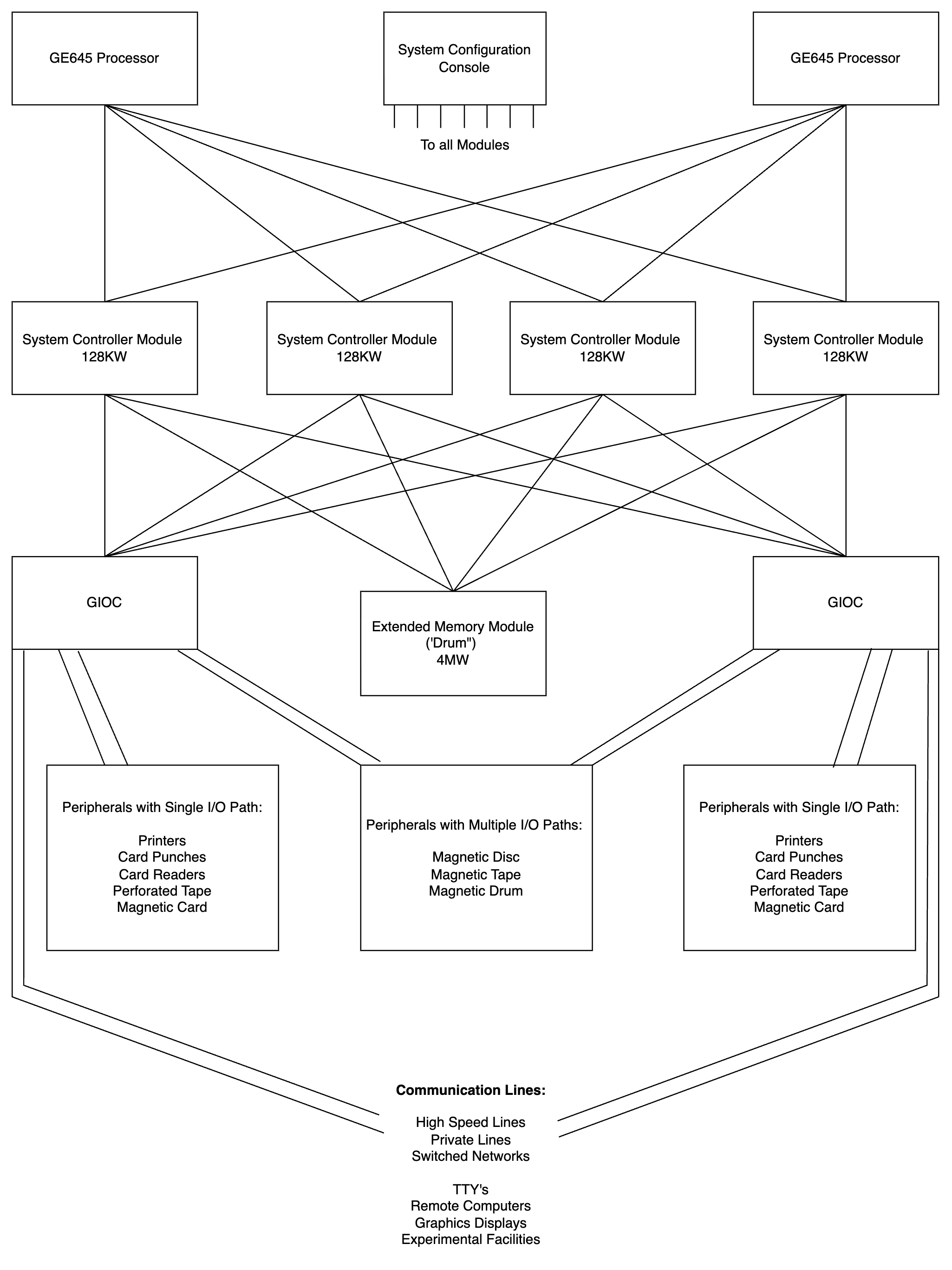
GE 645
The GE 645 mainframe computer was a development of the GE 635 for use in the Multics project. This was the first computer that implemented a configurable hardware protected memory system. It was designed to satisfy the requirements of Project MAC to develop a platform that would host their proposed next generation time-sharing operating system (Multics) and to meet the requirements of a theorized computer utility. The system was the first truly symmetric multiprocessing machine to use virtual memory, it was also among the first machines to implement what is now known as a translation lookaside buffer, the foundational patent for which was granted to John Couleur and Edward Glaser. General Electric initially publicly announced the GE 645 at the Fall Joint Computer Conference in November 1965. At a subsequent press conference in December of that year it was announced that they would be working towards "broad commercial availability" of the system. However they would subsequent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Honeywell 6180
The Honeywell 6000 series computers were a further development (using integrated circuits) of General Electric's 600-series mainframes manufactured by Honeywell International, Inc. from 1970 to 1989. Honeywell acquired the line when it purchased GE's computer division in 1970 and continued to develop them under a variety of names for many years. In 1989, Honeywell sold its computer division to the French company Groupe Bull who continued to market compatible machines. Models The high-end model was the 6080, with performance approximately 1 MIPS. Smaller models were the 6070, 6060, 6050, 6040, and 6030. In 1973, a low-end 6025 was introduced. The models with an even number as the next-to-last digit of the model number included an ''Enhanced Instruction Set'' feature (EIS), which added decimal arithmetic and storage-to-storage operations to the original word-oriented architecture. In 1973, Honeywell introduced the 6180, a 6000-series machine with addressing modifications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |