|
Hashing
Hash, hashes, hash mark, or hashing may refer to: Substances * Hash (food), a coarse mixture of ingredients, often based on minced meat * Hash (stew), a pork and onion-based gravy found in South Carolina * Hash, a nickname for hashish, a cannabis product Hash mark * Hash mark (sports), a marking on hockey rinks and gridiron football fields * Hatch marks, hash marks or tick marks, a form of mathematical notation * Number sign (#), also known as the hash, hash mark, or (in American English) pound sign * Service stripe, a military and paramilitary decoration * Tally mark, a counting notation * Checkmate symbol in chess Computing * Hash function, an encoding of data into a small, fixed size; used in hash tables and cryptography ** Hash table, a data structure using hash functions ** Cryptographic hash function, a hash function used to authenticate message integrity * URI fragment, in computer hypertext, a string of characters that refers to a subordinate resource * Geohash, a spat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Table
In computer science, a hash table is a data structure that implements an associative array, also called a dictionary or simply map; an associative array is an abstract data type that maps Unique key, keys to Value (computer science), values. A hash table uses a hash function to compute an ''index'', also called a ''hash code'', into an array of ''buckets'' or ''slots'', from which the desired value can be found. During lookup, the key is hashed and the resulting hash indicates where the corresponding value is stored. A map implemented by a hash table is called a hash map. Most hash table designs employ an Perfect hash function, imperfect hash function. Hash collision, Hash collisions, where the hash function generates the same index for more than one key, therefore typically must be accommodated in some way. In a well-dimensioned hash table, the average time complexity for each lookup is independent of the number of elements stored in the table. Many hash table designs also ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Function
A hash function is any Function (mathematics), function that can be used to map data (computing), data of arbitrary size to fixed-size values, though there are some hash functions that support variable-length output. The values returned by a hash function are called ''hash values'', ''hash codes'', (''hash/message'') ''digests'', or simply ''hashes''. The values are usually used to index a fixed-size table called a ''hash table''. Use of a hash function to index a hash table is called ''hashing'' or ''scatter-storage addressing''. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Hashing is a computationally- and storage-space-efficient form of data access that avoids the non-constant access time of ordered and unordered lists and s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash House Harriers
The Hash House Harriers (HHH or H3) is an international group of non-competitive running social clubs. An event organized by a club is known as a Hash or Run, or a Hash Run. A common denominal verb for this activity is Hashing, with participants calling themselves Hashers. Members are referred to as Harriers or Harriettes based on gender or preference. The Hash is humorously known as ''A Drinking Club With A Running Problem,'' with the preferred beverage of consumption being beer. History Hashing originated in December 1938 in Kuala Lumpur, Selangor, then in the Federated Malay States (now Malaysia). A group of British people, British immigrants began meeting on Friday evenings, to run in a fashion patterned after the traditional British game of paper chase (game), hare and hounds, in which one or two "hare" runners scatter a trail of cut paper for the "hounds" to track. Apart from the excitement of chasing the hare and finding the trail, Harriers reaching the end of the trail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map (mathematics), map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptography, cryptographic application: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (as for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is infeasible, ''assuming all input strings are equally likely.'' The ''resistance'' to such search is quantified as security strength: a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits, unless the space of possible input values is significantly smaller than 2^ (a practical example can be found in ); * a ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
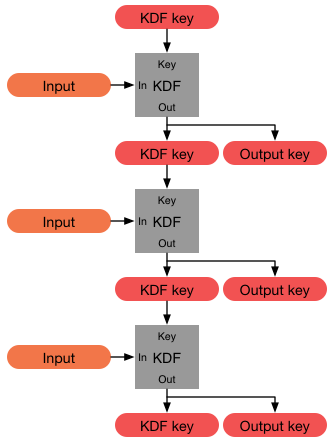
Password Hash
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation. History The first deliberately slow (key stretching) password-based key derivation function was called "crypt" (or "crypt(3)" after its man page), and was invented by Robert Morris in 1978. It would encrypt a constant (zero), using the first 8 characters of the user's password as the key, by performing 25 iterations of a modified DES encryption algorithm (in which a 12-bit nu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Geohash
Geohash is a public domain geocode system invented in 2008 by Gustavo Niemeyer * * * which encodes a geographic location into a short string of letters and digits. Similar ideas were introduced by G.M. Morton in 1966. It is a hierarchical spatial data structure which subdivides space into buckets of grid shape, which is one of the many applications of what is known as a Z-order curve, and generally space-filling curves. Geohashes offer properties like arbitrary precision and the possibility of gradually removing characters from the end of the code to reduce its size (and gradually lose precision). Geohashing guarantees that the longer a shared prefix between two geohashes is, the spatially closer they are together. The reverse of this is not guaranteed, as two points can be very close but have a short or no shared prefix. History The core part of the Geohash algorithm and the first initiative to similar solution was documented in a report of G.M. Morton in 1966, "A Compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zobrist Hashing
Zobrist hashing (also referred to as Zobrist keys or Zobrist signatures Bruce Moreland/ref>) is a hash function construction used in computer programs that play abstract board games, such as chess and Go, to implement transposition tables, a special kind of hash table that is indexed by a board position and used to avoid analyzing the same position more than once. Zobrist hashing is named for its inventor, Albert Lindsey Zobrist. It has also been applied as a method for recognizing substitutional alloy configurations in simulations of crystalline materials. Zobrist hashing is the first known instance of the generally useful underlying technique called tabulation hashing. Calculation of the hash value Zobrist hashing starts by randomly generating bitstrings for each possible element of a board game, i.e. for each combination of a piece and a position (in the game of chess, that's 6 pieces × 2 colors × 64 board positions, with a constant number of additional bitstrings for ca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash (food)
Hash is a dish consisting of chopped meat, potatoes, and fried onions. The name is derived from French language, French , meaning 'to chop'. Canned corned beef hash became especially popular in countries such as Britain and France during and after the Second World War as rationing limited the availability of fresh meat. Hash may be served for breakfast, lunch, or supper. When served for breakfast in the United States, hash may come with eggs, toast, hollandaise sauce, or baked beans. High-end restaurants offer sophisticated hash dishes on their menus. Modern preparations have been made with unconventional ingredients such as lamb, fish, venison, turkey, chicken, shrimp, or steak. United States "Hash" of many forms was part of the Standard American diet, American diet since at least the 18th century, as is attested by the availability of numerous recipes and the existence of many "hash houses" named after the dish. William Rice, Chicago Tribune In the United States, Sep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash House (other)
Hash House may refer to: * Hash House a go go, a restaurant chain * Hash House Bikers, an international group of non-competitive bicycling, social clubs * Hash House Harriers, an international group of non-competitive running, social clubs * John T. Hash House, a historic home in Dayton, Oregon * Hash House Hemp Products, a hemp retailer located in Lake Havasu City, Arizona {{disambiguation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Browns
Hash browns, also spelled hashed browns and hashbrowns, are a popular American breakfast food consisting of finely julienned potatoes that have been fried until golden brown. Hash browns are a staple breakfast item at diners in North America, where they are often fried on a large, common cooktop or grill. Hash browns are a popular mass-produced product sold in refrigerated, frozen and dehydrated forms. Etymology The word ''hash'' is derived from the French word , which means 'to hack' or 'to chop'. In other words, hashed brown potatoes can be interpreted literally as "chopped and fried potatoes". History The following recipe for "brown hashed potatoes" appears in the 1835 edition of the ''Minnesota Farmers' Institute Annual'': Cited b''The Old Foodie'' whose article is cited b''TastingTable'' Hash browns first started appearing on breakfast menus in New York City in the 1890s. The name was gradually changed to "hash-brown potatoes". Preparation A chef may prepare h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash (EP)
'' ' (read as "hash") is the second extended play by South Korean girl group Loona. It was released on February 5, 2020, by Blockberry Creative and distributed by Kakao M. Background On March 31, 2019, a teaser titled "#" was released on the group's official YouTube channel. The clip looks back to Loona's previous releases and teaser films and ends with the word "burn". It also features imagery of butterflies, as well as the symbols "++" and "xx". On May 31, a second teaser was released titled "La Maison Loona", with the phrase "delayed but someday" showed at the end. On December 13, a teaser titled "#1" was released. On December 31, an image teaser was released. On January 8, 2020, it was announced that member HaSeul would halt activities with the group due to health concerns. On January 10, a second teaser was released titled "#2", setting the release date to February 5. On January 13, individual teasers started to being released, starting with member HyeJu (formerly Olivi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Chain
A hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method used to produce many one-time keys from a single key or password. For non-repudiation, a hash function can be applied successively to additional pieces of data in order to record the chronology of data's existence. Definition A hash chain is a successive application of a cryptographic hash function h to a string x. For example, h(h(h(h(x)))) gives a hash chain of length 4, often denoted h^(x) Applications Leslie LamportL. Lamport, “Password Authentication with Insecure Communication”, Communications of the ACM 24.11 (November 1981), pp 770-772/ref> suggested the use of hash chains as a password protection scheme in an insecure environment. A server which needs to provide authentication may store a hash chain rather than a plain text password and prevent theft of the password in transmission or theft from the server. For exa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |