|
Cyber Essentials
Cyber Essentials is a United Kingdom certification scheme designed to show an organisation has a minimum level of protection in cyber security through annual assessments to maintain certification. Backed by the UK government and overseen by the National Cyber Security Centre (NCSC). It encourages organisations to adopt good practices in information security. Cyber Essentials also includes an assurance framework and a simple set of security controls to protect information from threats coming from the internet. The certification underwent substantial changes in January 2022 which included bringing all cloud services into scope and changes to the requirements on multi-factor authentication, passwords and pins. Certification The Cyber Essentials program provides two levels, the first is self-certification and the second requires independent validation of claims made: Cyber Essentials Commonly referred to as mark your own homework, organisations self-assess their systems, and then ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United Kingdom
The United Kingdom of Great Britain and Northern Ireland, commonly known as the United Kingdom (UK) or Britain, is a country in Europe, off the north-western coast of the continental mainland. It comprises England, Scotland, Wales and Northern Ireland. The United Kingdom includes the island of Great Britain, the north-eastern part of the island of Ireland, and many smaller islands within the British Isles. Northern Ireland shares a land border with the Republic of Ireland; otherwise, the United Kingdom is surrounded by the Atlantic Ocean, the North Sea, the English Channel, the Celtic Sea and the Irish Sea. The total area of the United Kingdom is , with an estimated 2020 population of more than 67 million people. The United Kingdom has evolved from a series of annexations, unions and separations of constituent countries over several hundred years. The Treaty of Union between the Kingdom of England (which included Wales, annexed in 1542) and the Kingdom of Scotland in 170 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Department For Business, Innovation And Skills
, type = Department , logo = Department for Business, Innovation and Skills logo.svg , logo_width = 200px , logo_caption = , picture = File:Лондан. 2014. Жнівень 26.JPG , seal = , seal_width = , seal_caption = , formed = 5 June 2009 , , preceding1 = Department for Business, Enterprise and Regulatory Reform Department for Innovation, Universities and Skills , dissolved = 14 July 2016 , superseding = Department for Business, Energy and Industrial Strategy; Department for International Trade , jurisdiction = United Kingdom , headquarters = 1, Victoria Street, London , employees = , budget = £16.5 billion (current) and £1.3 billion (capital) for 2011-12 , minister1_name = , minister1_pfo = , chief1_name = , chief1_position = , chief2_name = , chief2_position = , child1_agency = Companies House , child2_agency = HM Land Registry , child3_age ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security In The United Kingdom
A computer is a machine that can be programmed to carry out sequences of arithmetic or logical operations (computation) automatically. Modern digital electronic computers can perform generic sets of operations known as programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devices like personal computers and mobile devices like smartphones. Computers power the Internet, which links bill ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UK Cyber Security Forum
The UK Cyber Security Forum is a social enterprise spanning the United Kingdom, representing small and medium-sized enterprises (SMEs) in the UK cyber sector. It is divided up into 20 regional cyber clusters which provide free membership and events for their members. It forms part of the UK cyber security community. The Forum has been praised by UK Government for helping to address the cyber skills gap faced by the U.K. The concept of providing regional cyber security clusters was then later supported and laid out by the U.K Government Cyber Security Strategy in late 2014. National news has reported on the effectiveness of the forum, especially in terms of aiding collaboration between UK cyber companies. There has been considerable coverage of certain cyber clusters such as the London London is the capital and largest city of England and the United Kingdom, with a population of just under 9 million. It stands on the River Thames in south-east England at the head of a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UK Cyber Security Community
The cyber security (or information assurance) community in the United Kingdom is diverse, with many stakeholders groups contributing to support the ''UK Cyber Security Strategy''. The following is a list of some of these stakeholders. Government According to a parliamentary committee the UK government is not doing enough to protect the nation against cyber attack. Cyber Aware Cyber Aware is a cross-government awareness and behaviour campaign which provides advice on the simple measures individuals can take to protect themselves from cyber crime. Department for Digital, Culture, Media and Sport The Department for Digital, Culture, Media and Sport is one of the lead government departments on cyber security policy, responsible for supporting & promoting the UK cyber security sector, promoting cyber security research and innovation, and working with the National Cyber Security Centre to help ensure all UK organisations are secure online and resilient to cyber threats. Get Sa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
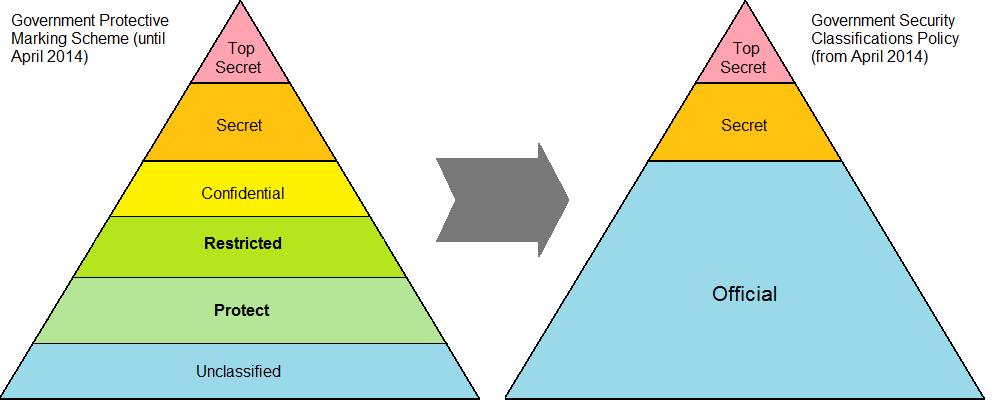
Government Security Classifications Policy
The Government Security Classifications Policy (GSCP) is a system for classifying sensitive government data in the United Kingdom. GPMS Historically, the Government Protective Marking Scheme was used by government bodies in the UK; it divides data into UNCLASSIFIED, PROTECT, RESTRICTED, CONFIDENTIAL, SECRET and TOP SECRET. This system was designed for paper-based records; it is not easily adapted to modern government work and is not widely understood. Current classifications The GSCP uses three levels of classification: OFFICIAL, SECRET and TOP SECRET. This is simpler than the old model and there is no direct relationship between the old and new classifications. "Unclassified" is deliberately omitted from the new model. Government bodies are not expected to automatically remark existing data, so there may be cases where organisations working under the new system still handle some data marked according to the old system. Information Asset Owners continue to be responsible for inf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Government Digital Service
The Government Digital Service is a unit of the Government of the United Kingdom's Cabinet Office tasked with transforming the provision of online public services. It was formed in April 2011 to implement the "Digital by Default" strategy proposed by a report produced for the Cabinet Office in 2010 called 'Directgov 2010 and beyond: revolution not evolution'. It is overseen by the Public Expenditure Executive (Efficiency & Reform). GDS is primarily based in the Whitechapel Building, London. Its CEO is Tom Read. GOV.UK On 20 July 2010, Directgov, the citizen services website, was moved to the Cabinet Office from the Department for Work and Pensions. From 1 April 2011 Directgov became part of the Government Digital Service, along with the BusinessLink website aimed at business users. On 13 September 2012, through a notice on the Directgov homepage, it was announced that the GOV.UK project, built by the Government Digital Service, would replace Directgov as the primary citizen web ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GovAssure
GovAssure is a new cybersecurity regime for the UK government, starting in 2023. History The process was announced in 2022. Compared to previous cybersecurity for UK government bodies, the main change is the adoption of the NCSC's Cyber Assessment Framework. GovAssure is expected to help organisations guard against rising Russian attacks, as well as new types of threat actors. The first two departments to be assessed under the new scheme are the Department for Business, Energy, and Industrial Strategy The Department for Business, Energy and Industrial Strategy (BEIS) is a department of His Majesty's Government. The department was formed during a machinery of government change on 14 July 2016, following Theresa May's appointment as Prime M ... and the Home Office, with C3IA assessing a selection of three systems at each. Processes * Government departments and some other public-sector organisations, will have their cybersecurity reviewed under the GovAssure process; * The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Assessment Framework
The Cyber Assessment Framework is a mechanism designed by NCSC for assuring the security of organisations. The CAF is tailored towards the needs of Critical National Infrastructure, to meet the NIS regulations, but the objectives can be used by other organisations. In addition to national public-sector and infrastructure bodies, the CAF is also being used by local government. Principles The CAF has fourteen objectives, grouped into four categories: These set high-level objectives which fit the needs of organisations handling high-impact data or performing essential functions. These have some similarities, but are not identical, to the categories of controls used by ISO 27001:2013. Objective A: Managing security risk * A.1 Governance * A.2 Risk management * A.3 Asset management * A.4 Supply chain Objective B: Protecting against cyber attack * B.1 Service protection policies and procedures * B.2 Identity and access control * B.3 Data security * B.4 System security * B.5 Resilient ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communications-Electronics Security Group
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primarily based at "The Doughnut" in the suburbs of Cheltenham, GCHQ is the responsibility of the country's Secretary of State for Foreign and Commonwealth Affairs (Foreign Secretary), but it is not a part of the Foreign Office and its Director ranks as a Permanent Secretary. GCHQ was originally established after the First World War as the Government Code and Cypher School (GC&CS) and was known under that name until 1946. During the Second World War it was located at Bletchley Park, where it was responsible for breaking the German Enigma codes. There are two main components of the GCHQ, the Composite Signals Organisation (CSO), which is responsible for gathering information, and the National Cyber Security Centre (NCSC), ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multi-factor Authentication
Multi-factor authentication (MFA; encompassing two-factor authentication, or 2FA, along with similar terms) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is). MFA protects user data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password. A ''third-party authenticator'' (TPA) app enables two-factor authentication, usually by showing a randomly generated and frequently changing code to use for authentication. Factors Authentication takes place when someone tries to log into a computer resource (such as a network, device, or application). The resource requires the u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Thin Client
In computer networking, a thin client is a simple (low-performance) computer that has been optimized for establishing a remote connection with a server-based computing environment. They are sometimes known as ''network computers'', or in their simplest form as ''zero clients''. The server does most of the work, which can include launching software programs, performing calculations, and storing data. This contrasts with a rich client or a conventional personal computer; the former is also intended for working in a client–server model but has significant local processing power, while the latter aims to perform its function mostly locally. Thin clients occur as components of a broader computing infrastructure, where many clients share their computations with a server or server farm. The server-side infrastructure uses cloud computing software such as application virtualization, hosted shared desktop (HSD) or desktop virtualization (VDI). This combination forms what is know ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |