|
Blue Pill (software)
Blue Pill is the codename for a rootkit based on x86 virtualization. Blue Pill originally required AMD-V (Pacifica) virtualization support, but was later ported to support Intel VT-x (Vanderpool) as well. It was designed by Joanna Rutkowska and originally demonstrated at the Black Hat Briefings on August 3, 2006, with a reference implementation for the Microsoft Windows Vista kernel. The name is a reference to the red pill and blue pill concept from the 1999 film '' The Matrix''. Overview The Blue Pill concept is to trap a running instance of the operating system by starting a thin hypervisor and virtualizing the rest of the machine under it. The previous operating system would still maintain its existing references to all devices and files, but nearly anything, including hardware interrupts, requests for data and even the system time could be intercepted (and a fake response sent) by the hypervisor. The original concept of Blue Pill was published by another researcher at IE ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software. The term ''rootkit'' is a compound of "root" (the traditional name of the privileged account on Unix-like operating systems) and the word "kit" (which refers to the software components that implement the tool). The term "rootkit" has negative connotations through its association with malware. Rootkit installation can be automated, or an attacker can install it after having obtained root or administrator access. Obtaining this access is a result of direct attack on a system, i.e. exploiting a vulnerability (such as privilege escalation) or a password (obtained by cracking or social engineering tactics like "phishing"). Once installed, it becomes possible to hide the intrusion as well as to maintain privileged ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
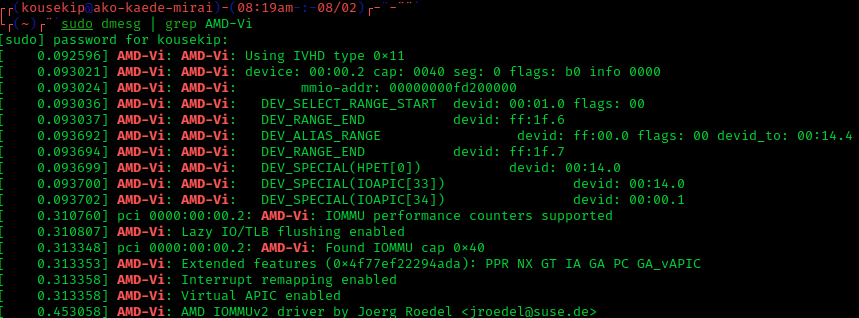
X86 Virtualization
x86 virtualization is the use of hardware-assisted virtualization capabilities on an x86/x86-64 CPU. In the late 1990s x86 virtualization was achieved by complex software techniques, necessary to compensate for the processor's lack of hardware-assisted virtualization capabilities while attaining reasonable performance. In 2005 and 2006, both Intel ( VT-x) and AMD (AMD-V) introduced limited hardware virtualization support that allowed simpler virtualization software but offered very few speed benefits. Greater hardware support, which allowed substantial speed improvements, came with later processor models. Software-based virtualization The following discussion focuses only on virtualization of the x86 architecture protected mode. In protected mode the operating system kernel runs at a higher privilege such as ring 0, and applications at a lower privilege such as ring 3. In software-based virtualization, a host OS has direct access to hardware while the guest OSs have limited a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AMD-V
x86 virtualization is the use of hardware-assisted virtualization capabilities on an x86/x86-64 CPU. In the late 1990s x86 virtualization was achieved by complex software techniques, necessary to compensate for the processor's lack of hardware-assisted virtualization capabilities while attaining reasonable performance. In 2005 and 2006, both Intel ( VT-x) and AMD ( AMD-V) introduced limited hardware virtualization support that allowed simpler virtualization software but offered very few speed benefits. Greater hardware support, which allowed substantial speed improvements, came with later processor models. Software-based virtualization The following discussion focuses only on virtualization of the x86 architecture protected mode. In protected mode the operating system kernel runs at a higher privilege such as ring 0, and applications at a lower privilege such as ring 3. In software-based virtualization, a host OS has direct access to hardware while the guest OSs have limite ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel VT-x
x86 virtualization is the use of hardware-assisted virtualization capabilities on an x86/x86-64 CPU. In the late 1990s x86 virtualization was achieved by complex software techniques, necessary to compensate for the processor's lack of hardware-assisted virtualization capabilities while attaining reasonable performance. In 2005 and 2006, both Intel ( VT-x) and AMD (AMD-V) introduced limited hardware virtualization support that allowed simpler virtualization software but offered very few speed benefits. Greater hardware support, which allowed substantial speed improvements, came with later processor models. Software-based virtualization The following discussion focuses only on virtualization of the x86 architecture protected mode. In protected mode the operating system kernel runs at a higher privilege such as ring 0, and applications at a lower privilege such as ring 3. In software-based virtualization, a host OS has direct access to hardware while the guest OSs have limited ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Joanna Rutkowska
Joanna Rutkowska (born 1981 in Warsaw) is a Polish computer security researcher, primarily known for her research on low-level security and stealth malware, and as founder of the Qubes OS security-focused desktop operating system. She became known in the security community after the Black Hat Briefings conference in Las Vegas in August 2006, where Rutkowska presented an attack against Vista kernel protection mechanism, and also a technique dubbed Blue Pill, that used hardware virtualization to move a running OS into a virtual machine. Subsequently, she has been named one of ''Five Hackers who Put a Mark on 2006'' by eWeek Magazine for her research on the topic. The original concept of Blue Pill was published by another researcher at IEEE Oakland in May 2006 under the name VMBR. During the following years, Rutkowska continued to focus on low-level security. In 2007 she demonstrated that certain types of hardware-based memory acquisition (e.g. FireWire based) are unreliable ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Black Hat Briefings
Black Hat Briefings (commonly referred to as Black Hat) is a computer security conference that provides security consulting, training, and briefings to hackers, corporations, and government agencies around the world. Black Hat brings together a variety of people interested in information security ranging from non-technical individuals, executives, hackers, and security professionals. The conference takes place regularly in Las Vegas, Barcelona, London and Riyadh. The conference has also been hosted in Amsterdam, Tokyo, and Washington, D.C. in the past. History The first Black Hat was held July 7-10, 1997 in Las Vegas, immediately prior to DEF CON 5. The conference was aimed at the computer industry, promising to give them privileged insight into the minds and motivations of their hacker adversaries. Its organizers stated: "While many conferences focus on information and network security, only the Black Hat Briefings will put your engineers and software programmers face-to-face ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Windows Vista
Windows Vista is a major release of the Windows NT operating system developed by Microsoft. It was the direct successor to Windows XP, which was released five years before, at the time being the longest time span between successive releases of Microsoft Windows desktop operating systems. Development was completed on November 8, 2006, and over the following three months, it was released in stages to computer hardware and software manufacturers, business customers and retail channels. On January 30, 2007, it was released internationally and was made available for purchase and download from the Windows Marketplace; it is the first release of Windows to be made available through a digital distribution platform. New features of Windows Vista include an updated graphical user interface and visual style dubbed Aero, a new search component called Windows Search, redesigned networking, audio, print and display sub-systems, and new multimedia tools such as Windows DVD Maker. Vista aimed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Pill And Blue Pill
The terms "red pill" and "blue pill" refer to a choice between the willingness to learn a potentially unsettling or life-changing truth by taking the red pill or remaining in contented ignorance with the blue pill. The terms are associated with the 1999 film ''The Matrix''. Background In ''The Matrix'', the main character Neo is offered the choice between a red pill and a blue pill by rebel leader Morpheus. Morpheus says "You take the blue pill... the story ends, you wake up in your bed and believe whatever you want to believe. You take the red pill... you stay in Wonderland, and I show you how deep the rabbit hole goes." The red pill represents an uncertain future and, unknown to Neo at the time he takes it, the pill frees him from the enslaving control of the machine-generated dream world. The pill allows Neo to escape into the real world, where he lives in a pod and is being used as a battery - and finds that living the "truth of reality" is harsher and more difficult th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Matrix
''The Matrix'' is a 1999 science fiction film, science fiction action film written and directed by the Wachowskis. It is the first installment in The Matrix (franchise), ''The Matrix'' film series, starring Keanu Reeves, Laurence Fishburne, Carrie-Anne Moss, Hugo Weaving, and Joe Pantoliano, and depicts a dystopian future in which humanity is unknowingly trapped inside the Matrix, a simulated reality that intelligent machines have created to distract humans while using their bodies as an energy source. When computer programmer Thomas Anderson, under the Security hacker, hacker alias "Neo (The Matrix), Neo", uncovers the truth, he joins a rebellion against the machines along with other people who have been freed from the Matrix. ''The Matrix'' is an example of the cyberpunk subgenre of science fiction. The Wachowskis' approach to action scenes was influenced by Anime, Japanese animation and martial arts films, and the film's use of Fight choreography, fight choreographers and wir ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hypervisor
A hypervisor (also known as a virtual machine monitor, VMM, or virtualizer) is a type of computer software, firmware or hardware that creates and runs virtual machines. A computer on which a hypervisor runs one or more virtual machines is called a ''host machine'', and each virtual machine is called a ''guest machine''. The hypervisor presents the guest operating systems with a virtual operating platform and manages the execution of the guest operating systems. Unlike an emulator, the guest executes most instructions on the native hardware. Multiple instances of a variety of operating systems may share the virtualized hardware resources: for example, Linux, Windows, and macOS instances can all run on a single physical x86 machine. This contrasts with operating-system–level virtualization, where all instances (usually called ''containers'') must share a single kernel, though the guest operating systems can differ in user space, such as different Linux distributions with the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timing Attack
In cryptography, a timing attack is a side-channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute cryptographic algorithms. Every logical operation in a computer takes time to execute, and the time can differ based on the input; with precise measurements of the time for each operation, an attacker can work backwards to the input. Finding secrets through timing information may be significantly easier than using cryptanalysis of known plaintext, ciphertext pairs. Sometimes timing information is combined with cryptanalysis to increase the rate of information leakage. Information can leak from a system through measurement of the time it takes to respond to certain queries. How much this information can help an attacker depends on many variables: cryptographic system design, the CPU running the system, the algorithms used, assorted implementation details, timing attack countermeasures, the accuracy of the timing measurements, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Week
''Bloomberg Businessweek'', previously known as ''BusinessWeek'', is an American weekly business magazine published fifty times a year. Since 2009, the magazine is owned by New York City-based Bloomberg L.P. The magazine debuted in New York City in September 1929. Bloomberg Businessweek business magazines are located in the Bloomberg Tower, 731 Lexington Avenue, Manhattan in New York City and market magazines are located in the Citigroup Center, 153 East 53rd Street between Lexington and Third Avenue, Manhattan in New York City. History ''Businessweek'' was first published based in New York City in September 1929, weeks before the stock market crash of 1929. The magazine provided information and opinions on what was happening in the business world at the time. Early sections of the magazine included marketing, labor, finance, management and Washington Outlook, which made ''Businessweek'' one of the first publications to cover national political issues that directly impacted ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |