|
Bullrun (code Name)
Bullrun (stylized BULLRUN) is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by ''The Guardian'', the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques. Information about the program's existence was leaked in 2013 by Edward Snowden. Although Snowden's documents do not contain technical information on exact cryptanalytic capabilities because Snowden did not have clearance access to such information, they do contain a 2010 GCHQ presentation which claims that "vast amounts of encrypted Internet data which have up till now been discarded are now exploitable". A nu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Classification Guide For Project BULLRUN
Classification is a process related to categorization, the process in which ideas and objects are recognized, differentiated and understood. Classification is the grouping of related facts into classes. It may also refer to: Business, organizations, and economics * Classification of customers, for marketing (as in Master data management) or for profitability (e.g. by Activity-based costing) * Classified information, as in legal or government documentation * Job classification, as in job analysis * Standard Industrial Classification, economic activities Mathematics * Attribute-value system, a basic knowledge representation framework * Classification theorems in mathematics * Class (set theory), Mathematical classification, grouping mathematical objects based on a property that all those objects share * Statistical classification, identifying to which of a set of categories a new observation belongs, on the basis of a training set of data Media * Classification (literature), a f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communications Security Establishment
The Communications Security Establishment (CSE; french: Centre de la sécurité des télécommunications, ''CST''), formerly (from 2008-2014) called the Communications Security Establishment Canada (CSEC), is the Government of Canada's national cryptologic agency. It is responsible for foreign signals intelligence (SIGINT) and communications security (COMSEC), protecting federal government electronic information and communication networks, and is the technical authority for cyber security and information assurance. Administered under the Department of National Defence (DND), the CSE is accountable to the Minister of National Defence through its deputy head, the Chief of CSE. The National Defence Minister is in turn accountable to the Cabinet and Parliament. The current Chief of the CSE is Caroline Xavier, who assumed the office on 31 August 2022. The Agency recently built a new headquarters and campus encompassing . The new headquarters totals a little over and is adjacent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Sockets Layer
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications. In technical writing you often you will see references to (D)TLS when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first defined in 1999, and the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground". Longstanding controversy surrounds the meaning of the term " hacker." In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". History Birth of subc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the firmware of the hardware, or parts of an operating system such as Windows. Trojan horses can be used to create vulnerabilities in a device. A Trojan horse may appear to be an entirely legitim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Escrow
Key escrow (also known as a "fair" cryptosystem) is an arrangement in which the keys needed to decrypt encrypted data are held in escrow so that, under certain circumstances, an authorized third party may gain access to those keys. These third parties may include businesses, who may want access to employees' secure business-related communications, or governments, who may wish to be able to view the contents of encrypted communications (also known as ''exceptional access''). The technical problem is a largely structural one. Access to protected information must be provided ''only'' to the intended recipient and at least one third party. The third party should be permitted access only under carefully controlled conditions, as for instance, a court order. Thus far, no system design has been shown to meet this requirement fully on a technical basis alone. All proposed systems also require correct functioning of some social linkage, as for instance the process of request for access, e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bernstein V
Bernstein is a common surname in the German language, meaning "amber" (literally "burn stone"). The name is used by both Germans and Jews, although it is most common among people of Ashkenazi Jewish heritage. The German pronunciation is , but in English it is pronounced either as or . Notable people sharing the surname "Bernstein" A–H * Aaron Bernstein (1812–1884), German short story writer and historian * Abe Bernstein (1892–1968), American mobster * Abraham Bernstein (other), several people * Adam Bernstein (born 1960), American film, music video, television director, and screenwriter * Al Bernstein (born 1950), American sportscaster, writer, stage performer, recording artist, and speaker * Al Bernstein (born 1949), Austrian contemporary artist * Al Bernstein (born 1950), American boxing commentator * Alan Bernstein (born 1947), Canadian medical researcher * Alexander Bernstein, Baron Bernstein of Craigweil (1936–2010), British television executive and politi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Export Of Cryptography From The United States
The export of cryptography from the United States to other countries has experienced various levels of restrictions over time. World War II illustrated that code-breaking and cryptography can play an integral part in national security and the ability to prosecute war. Changes in technology and the preservation of free speech have been competing factors in the regulation and constraint of cryptographic technologies for export. History Cold War era In the early days of the Cold War, the U.S. and its allies developed an elaborate series of export control regulations designed to prevent a wide range of Western technology from falling into the hands of others, particularly the Eastern bloc. All export of technology classed as 'critical' required a license. CoCom was organized to coordinate Western export controls. Two types of technology were protected: technology associated only with weapons of war ("munitions") and dual use technology, which also had commercial applications. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberspace Electronic Security Act
The Cyberspace Electronic Security Act of 1999 (CESA) is a bill proposed by the Clinton administration during the 106th United States Congress that enables the government to harvest keys used in encryption. The Cyberspace Electronic Security Act gives law enforcement the ability to gain access to encryption keys and cryptography methods. The initial version of this act enabled federal law enforcement agencies to secretly use monitoring, electronic capturing equipments and other technologies to access and obtain information. These provisions were later stricken from the act, although federal law enforcement agencies still have a significant degree of latitude to conduct investigations relating to electronic information. The act generated discussion about what capabilities should be allowed to law enforcement in the detection of criminal activity. After vocal objections from civil liberties groups, the administration backed away from the controversial bill. See also *Computer securi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communications Assistance For Law Enforcement Act
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 USC 1001-1010). CALEA's purpose is to enhance the ability of law enforcement agencies to conduct lawful interception of communication by requiring that telecommunications carriers and manufacturers of telecommunications equipment modify and design their equipment, facilities, and services to ensure that they have built-in capabilities for targeted surveillance, allowing federal agencies to selectively wiretap any telephone traffic; it has since been extended to cover broadband Internet and VoIP traffic. Some government agencies argue that it covers mass surveillance of communications rather than just tapping specific lines and that not all CALEA-based access requires a warrant. The original reason for adopting CALEA was the Federal Burea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Skipjack (cipher)
In cryptography, Skipjack is a block cipher—an algorithm for encryption—developed by the U.S. National Security Agency (NSA). Initially classified, it was originally intended for use in the controversial Clipper chip. Subsequently, the algorithm was declassified. History of Skipjack Skipjack was proposed as the encryption algorithm in a US government-sponsored scheme of key escrow, and the cipher was provided for use in the Clipper chip, implemented in tamperproof hardware. Skipjack is used only for encryption; the key escrow is achieved through the use of a separate mechanism known as the Law Enforcement Access Field (LEAF). The algorithm was initially secret, and was regarded with considerable suspicion by many for that reason. It was declassified on 24 June 1998, shortly after its basic design principle had been discovered independently by the public cryptography community. To ensure public confidence in the algorithm, several academic researchers from outside the g ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Clipper Chip
The Clipper chip was a chipset that was developed and promoted by the United States National Security Agency (NSA) as an encryption device that secured "voice and data messages" with a built-in backdoor that was intended to "allow Federal, State, and local law enforcement officials the ability to decode intercepted voice and data transmissions." It was intended to be adopted by telecommunications companies for voice transmission. Introduced in 1993, it was entirely defunct by 1996. Key escrow The Clipper chip used a data encryption algorithm called Skipjack to transmit information and the Diffie–Hellman key exchange-algorithm to distribute the cryptokeys between the peers. Skipjack was invented by the National Security Agency of the U.S. Government; this algorithm was initially classified SECRET, which prevented it from being subjected to peer review from the encryption research community. The government did state that it used an 80-bit key, that the algorithm was symmetri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
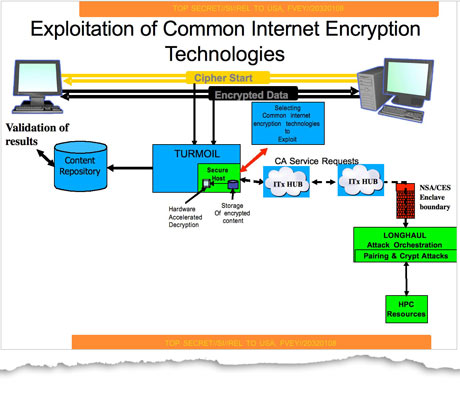



.jpg)
