|
Blom's Scheme
Blom's scheme is a symmetric threshold key exchange protocol in cryptography. The scheme was proposed by the Swedish cryptographer Rolf Blom in a series of articles in the early 1980s. A trusted party gives each participant a secret key and a public identifier, which enables any two participants to independently create a shared key for communicating. However, if an attacker can compromise the keys of at least k users, they can break the scheme and reconstruct every shared key. Blom's scheme is a form of threshold secret sharing. Blom's scheme is currently used by the HDCP (Version 1.x only) copy protection scheme to generate shared keys for high-definition content sources and receivers, such as HD DVD players and high-definition televisions. The protocol The key exchange protocol involves a trusted party (Trent) and a group of \scriptstyle n users. Let Alice and Bob be two users of the group. Protocol setup Trent chooses a random and secret symmetric matrix \scriptstyle D_ over ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Exchange
Key exchange (also key establishment) is a method in cryptography by which cryptographic keys are exchanged between two parties, allowing use of a cryptographic algorithm. If the sender and receiver wish to exchange encrypted messages, each must be equipped to encrypt messages to be sent and decrypt messages received. The nature of the equipping they require depends on the encryption technique they might use. If they use a code, both will require a copy of the same codebook. If they use a cipher, they will need appropriate keys. If the cipher is a symmetric key cipher, both will need a copy of the same key. If it is an asymmetric key cipher with the public/private key property, both will need the other's public key. Channel of exchange Key exchange is done either in-band or out-of-band. The key exchange problem The key exchange problem describes ways to exchange whatever keys or other information are needed for establishing a secure communication channel so that no one else ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Threshold Scheme
Secret sharing (also called secret splitting) refers to methods for distributing a secret among a group, in such a way that no individual holds any intelligible information about the secret, but when a sufficient number of individuals combine their 'shares', the secret may be reconstructed. Whereas ''insecure'' secret sharing allows an attacker to gain more information with each share, ''secure'' secret sharing is 'all or nothing' (where 'all' means the necessary number of shares). In one type of secret sharing scheme there is one ''dealer'' and ''n'' ''players''. The dealer gives a share of the secret to the players, but only when specific conditions are fulfilled will the players be able to reconstruct the secret from their shares. The dealer accomplishes this by giving each player a share in such a way that any group of ''t'' (for ''threshold'') or more players can together reconstruct the secret but no group of fewer than ''t'' players can. Such a system is called a -threshol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HDCP
High-bandwidth Digital Content Protection (HDCP) is a form of digital copy protection developed by Intel Corporation to prevent copying of digital audio and video content as it travels across connections. Types of connections include DisplayPort (DP), Digital Visual Interface (DVI), and High-Definition Multimedia Interface (HDMI), as well as less popular or now deprecated protocols like Gigabit Video Interface (GVIF) and Unified Display Interface (UDI). The system is meant to stop HDCP-encrypted content from being played on unauthorized devices or devices which have been modified to copy HDCP content. Before sending data, a transmitting device checks that the receiver is authorized to receive it. If so, the transmitter encrypts the data to prevent eavesdropping as it flows to the receiver. In order to make a device that plays HDCP-enabled content, the manufacturer must obtain a license for the patent from Intel subsidiary Digital Content Protection LLC, pay an annual fee, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HD DVD
HD DVD (short for High Definition Digital Versatile Disc) is an obsolete high-density optical disc format for storing data and playback of high-definition video. Supported principally by Toshiba, HD DVD was envisioned to be the successor to the standard DVD format. HD DVD employed a blue laser with a shorter wavelength (with the exception of the 3× DVD and HD REC variants), and it stored about 3.2 times as much data per layer as its predecessor (maximum capacity: 15 GB per layer compared to 4.7 GB per layer on a DVD). The format was commercially released in 2006 and fought a protracted format war with rival Blu-ray. On February 19, 2008, Toshiba abandoned the format, announcing it would no longer manufacture HD DVD players and drives. The HD DVD Promotion Group was dissolved on March 28, 2008. The HD DVD physical disc specifications (but not the codecs) were used as the basis for the China Blue High-definition Disc (CBHD) formerly called CH-DVD. History In the lat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
High-definition Television
High-definition television (HD or HDTV) describes a television system which provides a substantially higher image resolution than the previous generation of technologies. The term has been used since 1936; in more recent times, it refers to the generation following standard-definition television (SDTV), often abbreviated to HDTV or HD-TV. It is the current de facto standard video format used in most broadcasts: terrestrial broadcast television, cable television, satellite television and Blu-ray Discs. Formats HDTV may be transmitted in various formats: * 720p (1280 horizontal pixels × 720 lines): 921,600 pixels * 1080i (1920×1080) interlaced scan: 1,036,800 pixels (~1.04 MP). * 1080p (1920×1080) progressive scan: 2,073,600 pixels (~2.07 MP). ** Some countries also use a non-standard CEA resolution, such as 1440×1080i: 777,600 pixels (~0.78 MP) per field or 1,555,200 pixels (~1.56 MP) per frame When transmitted at two megapixels per frame, HDTV provides about five times ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alice And Bob
Alice and Bob are fictional characters commonly used as placeholders in discussions about cryptographic systems and protocols, and in other science and engineering literature where there are several participants in a thought experiment. The Alice and Bob characters were invented by Ron Rivest, Adi Shamir, and Leonard Adleman in their 1978 paper "A Method for Obtaining Digital Signatures and Public-key Cryptosystems". Subsequently, they have become common archetypes in many scientific and engineering fields, such as quantum cryptography, game theory and physics. As the use of Alice and Bob became more widespread, additional characters were added, sometimes each with a particular meaning. These characters do not have to refer to people; they refer to generic agents which might be different computers or even different programs running on a single computer. Overview Alice and Bob are the names of fictional characters used for convenience and to aid comprehension. For example, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Symmetric Matrix
In linear algebra, a symmetric matrix is a square matrix that is equal to its transpose. Formally, Because equal matrices have equal dimensions, only square matrices can be symmetric. The entries of a symmetric matrix are symmetric with respect to the main diagonal. So if a_ denotes the entry in the ith row and jth column then for all indices i and j. Every square diagonal matrix is symmetric, since all off-diagonal elements are zero. Similarly in characteristic different from 2, each diagonal element of a skew-symmetric matrix must be zero, since each is its own negative. In linear algebra, a real symmetric matrix represents a self-adjoint operator represented in an orthonormal basis over a real inner product space. The corresponding object for a complex inner product space is a Hermitian matrix with complex-valued entries, which is equal to its conjugate transpose. Therefore, in linear algebra over the complex numbers, it is often assumed that a symmetric matrix refe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Finite Field
In mathematics, a finite field or Galois field (so-named in honor of Évariste Galois) is a field that contains a finite number of elements. As with any field, a finite field is a set on which the operations of multiplication, addition, subtraction and division are defined and satisfy certain basic rules. The most common examples of finite fields are given by the integers mod when is a prime number. The ''order'' of a finite field is its number of elements, which is either a prime number or a prime power. For every prime number and every positive integer there are fields of order p^k, all of which are isomorphic. Finite fields are fundamental in a number of areas of mathematics and computer science, including number theory, algebraic geometry, Galois theory, finite geometry, cryptography and coding theory. Properties A finite field is a finite set which is a field; this means that multiplication, addition, subtraction and division (excluding division by zero) are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
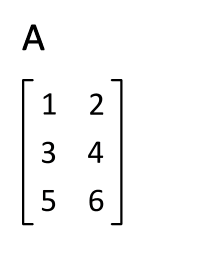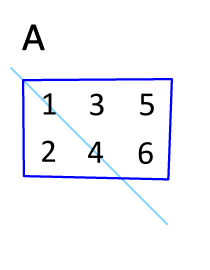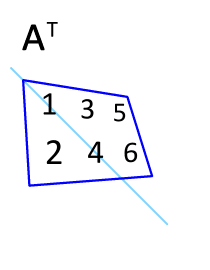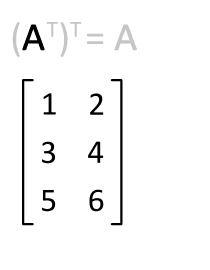
Matrix Transpose
In linear algebra, the transpose of a matrix is an operator which flips a matrix over its diagonal; that is, it switches the row and column indices of the matrix by producing another matrix, often denoted by (among other notations). The transpose of a matrix was introduced in 1858 by the British mathematician Arthur Cayley. In the case of a logical matrix representing a binary relation R, the transpose corresponds to the converse relation RT. Transpose of a matrix Definition The transpose of a matrix , denoted by , , , A^, , , or , may be constructed by any one of the following methods: # Reflect over its main diagonal (which runs from top-left to bottom-right) to obtain #Write the rows of as the columns of #Write the columns of as the rows of Formally, the -th row, -th column element of is the -th row, -th column element of : :\left mathbf^\operatorname\right = \left mathbf\right. If is an matrix, then is an matrix. In the case of square matrices, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reed–Solomon Error Correction
Reed–Solomon codes are a group of error-correcting codes that were introduced by Irving S. Reed and Gustave Solomon in 1960. They have many applications, the most prominent of which include consumer technologies such as MiniDiscs, CDs, DVDs, Blu-ray discs, QR codes, data transmission technologies such as DSL and WiMAX, broadcast systems such as satellite communications, DVB and ATSC, and storage systems such as RAID 6. Reed–Solomon codes operate on a block of data treated as a set of finite-field elements called symbols. Reed–Solomon codes are able to detect and correct multiple symbol errors. By adding = − check symbols to the data, a Reed–Solomon code can detect (but not correct) any combination of up to erroneous symbols, ''or'' locate and correct up to erroneous symbols at unknown locations. As an erasure code, it can correct up to erasures at locations that are known and provided to the algorithm, or it can detect and correct combinations of erro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CRC Press
The CRC Press, LLC is an American publishing group that specializes in producing technical books. Many of their books relate to engineering, science and mathematics. Their scope also includes books on business, forensics and information technology. CRC Press is now a division of Taylor & Francis, itself a subsidiary of Informa. History The CRC Press was founded as the Chemical Rubber Company (CRC) in 1903 by brothers Arthur, Leo and Emanuel Friedman in Cleveland, Ohio, based on an earlier enterprise by Arthur, who had begun selling rubber laboratory aprons in 1900. The company gradually expanded to include sales of laboratory equipment to chemists. In 1913 the CRC offered a short (116-page) manual called the ''Rubber Handbook'' as an incentive for any purchase of a dozen aprons. Since then the ''Rubber Handbook'' has evolved into the CRC's flagship book, the '' CRC Handbook of Chemistry and Physics''. In 1964, Chemical Rubber decided to focus on its publishing ventures ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |