|
Assembly (CLI)
An assembly in the Common Language Infrastructure (CLI) is a compiled code library used for deployment, versioning, and security. There are two types: process assemblies ( EXE) and library assemblies ( DLL). A process assembly represents a process that will use classes defined in library assemblies. CLI assemblies contain code in CIL, which is usually generated from a CLI language, and then compiled into machine language at run time by the just-in-time compiler. In the .NET Framework implementation, this compiler is part of the Common Language Runtime (CLR). An assembly can consist of one or more files. Code files are called modules. An assembly can contain more than one code module. And since it is possible to use different languages to create code modules, it is technically possible to use several different languages to create an assembly. Visual Studio however does not support using different languages in one assembly. Assembly names The name of an assembly consists o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Common Language Infrastructure
The Common Language Infrastructure (CLI) is an open specification and technical standard originally developed by Microsoft and standardized by International Organization for Standardization, ISO/International Electrotechnical Commission, IEC (ISO/IEC 23271) and Ecma International (ECMA 335) that describes executable code and a runtime environment that allows List of CLI languages, multiple high-level languages to be used on different Computing platform, computer platforms without being rewritten for specific architectures. This implies it is platform agnostic. The .NET Framework, .NET and Mono (software), Mono are implementations of the CLI. The metadata format is also used to specify the API definitions exposed by the Windows Runtime. Overview Among other things, the CLI specification describes the following five aspects: ;The Common Type System (CTS) :A set of data types and operations that are shared by all CTS-compliant programming languages. ;The Metadata (CLI), Metadata :In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map (mathematics), map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptography, cryptographic application: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (as for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is infeasible, ''assuming all input strings are equally likely.'' The ''resistance'' to such search is quantified as security strength: a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits, unless the space of possible input values is significantly smaller than 2^ (a practical example can be found in ); * a ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File System Permissions
Typically, a file system maintains permission settings for each stored item commonly files and directories that either grant or deny the ability to manipulate file system items. Often the settings allow controlling access based on function such as read, change, navigate, and execute and to different users and groups of users. One well-established technology was developed for Unix and later codified by POSIX. Another common technology is an access-control list (ACL) with multiple variants implemented in file systems and one codified by POSIX. Since POSIX defines both the older Unix-based technology as well as ACLs, the former is called ''traditional POSIX permissions'' for clarity even though it is not a well-known term. A permission-driven user interface tailors the functionality available to the user based on file system item permissions. For example, the interface might hide menu options that are not allowed based on the permissions stored for an item. Examples File sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sandbox (computer Security)
In computer security, a sandbox is a security mechanism for separating running programs, usually in an effort to mitigate system failures and/or software vulnerabilities from spreading. The sandbox metaphor derives from the concept of a child's sandbox—a play area where children can build, destroy, and experiment without causing any real-world damage. It is often used to kill untested or untrusted programs or code, possibly from unverified or untrusted third parties, suppliers, users or websites, without risking harm to the host machine or operating system. A sandbox typically provides a tightly controlled set of resources for guest programs to run in, such as storage and memory scratch space. Network access, the ability to inspect the host system, or read from input devices are usually disallowed or heavily restricted. In the sense of providing a highly controlled environment, sandboxes may be seen as a specific example of virtualization. Sandboxing is frequently used to t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
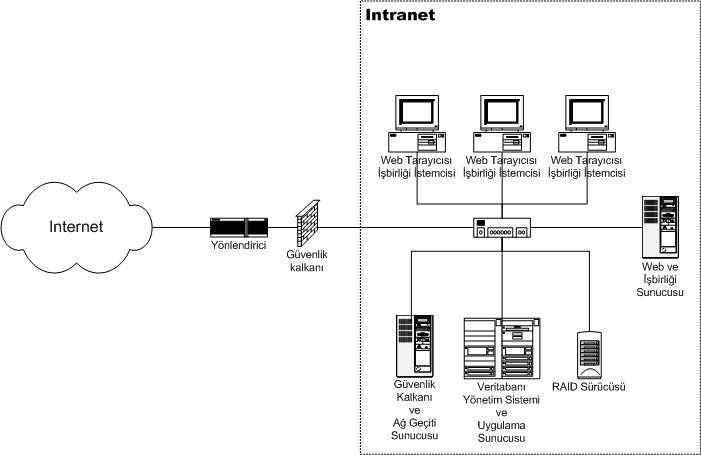
Intranet
An intranet is a computer network for sharing information, easier communication, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite. An organization-wide intranet can constitute an important focal point of internal communication and collaboration, and provide a single starting point to access internal and external resources. In its simplest form, an intranet is established with the technologies for local area networks (LANs) and wide area networks (WANs). Many modern intranets have Web search engine, search engines, user profiles, blogs, mobile apps with notifications, and events planning within their infrastructure. An intranet is sometimes contrasted to an extranet. While an intranet is generally restricted to employees of the organization, extranets ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Code Access Security
Code Access Security (CAS), in the Microsoft .NET framework, is Microsoft's solution to prevent untrusted code from performing privileged actions. When the CLR loads an assembly it will obtain evidence for the assembly and use this to identify the code group that the assembly belongs to. A code group contains a permission set (one or more permissions). Code that performs a privileged action will perform a code access demand which will cause the CLR to walk up the call stack and examine the permission set granted to the assembly of each method in the call stack. The code groups and permission sets are determined by the administrator of the machine who defines the security policy. Microsoft considers CAS as obsolete and discourages its use. It is also not available in .NET Core and .NET. Evidence Evidence can be any information associated with an assembly. The default evidences that are used by .NET code access security are: *Application directory: the directory in which an a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
White Hat (computer Security)
A white hat (or a white-hat hacker, a whitehat) is an ethical security hacker. Ethical hacking is a term meant to imply a broader category than just penetration testing. Under the owner's consent, white-hat hackers aim to identify any vulnerabilities or security issues the current system has. The white hat is contrasted with the black hat, a malicious hacker; this definitional dichotomy comes from Western films, where heroic and antagonistic cowboys might traditionally wear a white and a black hat, respectively. There is a third kind of hacker known as a grey hat who hacks with good intentions but at times without permission. White-hat hackers may also work in teams called " sneakers and/or hacker clubs", red teams, or tiger teams. History One of the first instances of an ethical hack being used was a "security evaluation" conducted by the United States Air Force, in which the Multics operating systems were tested for "potential use as a two-level (secret/top secret) system. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spoofing Attack
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage. Internet Spoofing and TCP/IP Many of the protocols in the TCP/IP suite do not provide mechanisms for authenticating the source or destination of a message, leaving them vulnerable to spoofing attacks when extra precautions are not taken by applications to verify the identity of the sending or receiving host. IP spoofing and ARP spoofing in particular may be used to leverage man-in-the-middle attacks against hosts on a computer network. Spoofing attacks which take advantage of TCP/IP suite protocols may be mitigated with the use of firewalls capable of deep packet inspection or by taking measures to verify the identity of the sender or recipient of a message. Domain name spoofing The term 'Domain name spoofing' (or simply though less accurately, 'Domain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Global Assembly Cache
The Global Assembly Cache (GAC) is a machine-wide CLI assembly cache for the Common Language Infrastructure (CLI) in Microsoft's .NET Framework. The approach of having a specially controlled central repository addresses the flaws in the shared library concept and helps to avoid pitfalls of other solutions that led to drawbacks like DLL hell. Requirements Assemblies residing in the GAC must adhere to a specific versioning scheme which allows for side-by-side execution of different code versions. Specifically, such assemblies must be strongly named. Usage There are two ways to interact with the GAC: the Global Assembly Cache Tool (gacutil.exe) and the Assembly Cache Viewer (shfusion.dll). Global Assembly Cache Tool gacutil.exe is an older command-line utility that shipped with .NET 1.1 and is still available with the .NET SDK. One can check the availability of a shared assembly in GAC by using the command: gacutil.exe /l One can register a shared assembly in the GAC by us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NTFS
NT File System (NTFS) (commonly called ''New Technology File System'') is a proprietary journaling file system developed by Microsoft in the 1990s. It was developed to overcome scalability, security and other limitations with File Allocation Table, FAT. NTFS adds several features that File Allocation Table, FAT and HPFS (file system), HPFS lack, including: access control lists (ACLs); filesystem encryption; transparent compression; sparse files; Journaling file system, file system journaling and shadow copy, volume shadow copy, a feature that allows backups of a system while in use. Starting with Windows NT 3.1, it is the default file system of the Windows NT family superseding the File Allocation Table (FAT) file system. NTFS read/write support is available on Linux and Berkeley Software Distribution, BSD using NTFS3 in Linux kernel, Linux and NTFS-3G in BSD. NTFS uses several files hidden from the user to store metadata about other files stored on the drive which can help impr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Allocation Table
File Allocation Table (FAT) is a file system developed for personal computers and was the default file system for the MS-DOS and Windows 9x operating systems. Originally developed in 1977 for use on floppy disks, it was adapted for use on Hard disk drive, hard disks and other devices. The increase in disk drive capacity over time drove modifications to the design that resulted in versions: #FAT12, FAT12, #FAT16, FAT16, #FAT32, FAT32, and exFAT. FAT was replaced with NTFS as the default file system on Microsoft operating systems starting with Windows XP. Nevertheless, FAT continues to be commonly used on relatively small capacity solid-state storage technologies such as SD card, MultiMediaCard (MMC) and eMMC because of its compatibility and ease of implementation. Uses Historical FAT was used on hard disk drive, hard disks throughout the DOS and Windows 9x eras. Microsoft introduced NTFS with the Windows NT platform in 1993, but FAT remained the standard for the home use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |