|
26-bit Computing
In computer architecture, 26-bit integers, memory addresses, or other data units are those that are 26 bits wide, and thus can represent unsigned values up to 67,108,863. Two examples of computer processors that featured 26-bit memory addressing are certain second generation IBM System/370 mainframe computer models introduced in 1981 (and several subsequent models), which had 26-bit physical addresses but had only the same 24-bit virtual addresses as earlier models, and the first generations of ARM processors. History IBM System/370 As data processing needs continued to grow, IBM and their customers faced challenges directly addressing larger memory sizes. In what ended up being a short-term "emergency" solution, a pair of IBM's second wave of System/370 models, the 3033 and 3081, introduced 26-bit real memory addressing, increasing the System/370's amount of physical memory that could be attached by a factor of 4 from the previous 24-bit limit of 16 MB. IBM referred to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Status Register
A status register, flag register, or condition code register (CCR) is a collection of status Flag (computing), flag bits for a Central processing unit, processor. Examples of such registers include FLAGS register (computing), FLAGS register in the x86 architecture, flags in the program status word (PSW) register in the IBM System/360 architecture through z/Architecture, and the application program status register (APSR) in the ARM Cortex-A architecture. The status register is a hardware register that contains information about the state of the Central processing unit, processor. Individual bits are implicitly or explicitly read and/or written by the machine code instructions executing on the processor. The status register lets an instruction take action contingent on the outcome of a previous instruction. Typically, flags in the status register are modified as effects of arithmetic and bit manipulation operations. For example, a Z bit may be set if the result of the operation is ze ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RISC OS
RISC OS () is an operating system designed to run on ARM architecture, ARM computers. Originally designed in 1987 by Acorn Computers of England, it was made for use in its new line of ARM-based Acorn Archimedes, Archimedes personal computers and was then shipped with other computers produced by the company. Despite the demise of Acorn, RISC OS continues to be developed today by the RISC OS Open community on version 5.0 of the system that was open sourced in 2018. RISC OS is a Modular programming, modular operating system and takes its name from the reduced instruction set computer (RISC) architecture it supports. It incorporates a graphical user interface and a windowing system. Between 1987 and 1998, RISC OS shipped with every ARM-based Acorn computer including the Archimedes line, Acorn's R line (with RISC iX as a dual-boot option), RiscPC, Acorn A7000, A7000, and prototype models such as the Acorn Acorn Computers#NewsPad, NewsPad and Phoebe (computer), Phoebe computer. A vers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
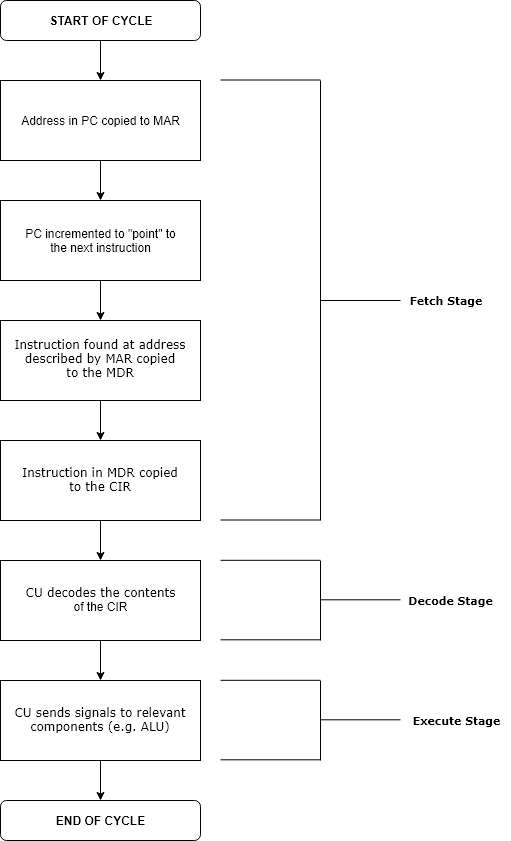
Execution (computers)
Execution in computer engineering, computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a "Instruction cycle, fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the Formal semantics of programming languages, semantics of those instructions. Programs for a computer may be executed in a Batch processing, batch process without human interaction or a User (computing), user may type Command (computing), commands in an Session (computer science), interactive session of an Interpreter (computing), interpreter. In this case, the "commands" are simply program instructions, whose executio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Access Memory
Random-access memory (RAM; ) is a form of electronic computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks and magnetic tape), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. In today's technology, random-access memory takes the form of integrated circuit (IC) chips with MOS (metal–oxide–semiconductor) memory cells. RAM is normally associated with volatile types of memory where stored information is lost if power is removed. The two main types of volatile random-access semiconductor memory are static ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Address Bus
In computer architecture, a bus (historically also called a data highway or databus) is a communication system that transfers data between components inside a computer or between computers. It encompasses both hardware (e.g., wires, optical fiber) and software, including communication protocols. At its core, a bus is a shared physical pathway, typically composed of wires, traces on a circuit board, or busbars, that allows multiple devices to communicate. To prevent conflicts and ensure orderly data exchange, buses rely on a communication protocol to manage which device can transmit data at a given time. Buses are categorized based on their role, such as system buses (also known as internal buses, internal data buses, or memory buses) connecting the CPU and memory. Expansion buses, also called peripheral buses, extend the system to connect additional devices, including peripherals. Examples of widely used buses include PCI Express (PCIe) for high-speed internal connectio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
32-bit Computing
In computer architecture, 32-bit computing refers to computer systems with a processor, memory, and other major system components that operate on data in a maximum of 32- bit units. Compared to smaller bit widths, 32-bit computers can perform large calculations more efficiently and process more data per clock cycle. Typical 32-bit personal computers also have a 32-bit address bus, permitting up to 4 GiB of RAM to be accessed, far more than previous generations of system architecture allowed. 32-bit designs have been used since the earliest days of electronic computing, in experimental systems and then in large mainframe and minicomputer systems. The first hybrid 16/32-bit microprocessor, the Motorola 68000, was introduced in the late 1970s and used in systems such as the original Apple Macintosh. Fully 32-bit microprocessors such as the HP FOCUS, Motorola 68020 and Intel 80386 were launched in the early to mid 1980s and became dominant by the early 1990s. This generat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interrupt
In digital computers, an interrupt (sometimes referred to as a trap) is a request for the processor to ''interrupt'' currently executing code (when permitted), so that the event can be processed in a timely manner. If the request is accepted, the processor will suspend its current activities, save its state, and execute a function called an '' interrupt handler'' (or an ''interrupt service routine'', ISR) to deal with the event. This interruption is often temporary, allowing the software to resume normal activities after the interrupt handler finishes, although the interrupt could instead indicate a fatal error. Interrupts are commonly used by hardware devices to indicate electronic or physical state changes that require time-sensitive attention. Interrupts are also commonly used to implement computer multitasking and system calls, especially in real-time computing. Systems that use interrupts in these ways are said to be interrupt-driven. History Hardware interrupts wer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subroutine
In computer programming, a function (also procedure, method, subroutine, routine, or subprogram) is a callable unit of software logic that has a well-defined interface and behavior and can be invoked multiple times. Callable units provide a powerful programming tool. The primary purpose is to allow for the decomposition of a large and/or complicated problem into chunks that have relatively low cognitive load and to assign the chunks meaningful names (unless they are anonymous). Judicious application can reduce the cost of developing and maintaining software, while increasing its quality and reliability. Callable units are present at multiple levels of abstraction in the programming environment. For example, a programmer may write a function in source code that is compiled to machine code that implements similar semantics. There is a callable unit in the source code and an associated one in the machine code, but they are different kinds of callable units with different impl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Program
A computer program is a sequence or set of instructions in a programming language for a computer to Execution (computing), execute. It is one component of software, which also includes software documentation, documentation and other intangible components. A ''computer program'' in its human-readable form is called source code. Source code needs another computer program to Execution (computing), execute because computers can only execute their native machine instructions. Therefore, source code may be Translator (computing), translated to machine instructions using a compiler written for the language. (Assembly language programs are translated using an Assembler (computing), assembler.) The resulting file is called an executable. Alternatively, source code may execute within an interpreter (computing), interpreter written for the language. If the executable is requested for execution, then the operating system Loader (computing), loads it into Random-access memory, memory and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ARM Architecture
ARM (stylised in lowercase as arm, formerly an acronym for Advanced RISC Machines and originally Acorn RISC Machine) is a family of reduced instruction set computer, RISC instruction set architectures (ISAs) for central processing unit, computer processors. Arm Holdings develops the ISAs and licenses them to other companies, who build the physical devices that use the instruction set. It also designs and licenses semiconductor intellectual property core, cores that implement these ISAs. Due to their low costs, low power consumption, and low heat generation, ARM processors are useful for light, portable, battery-powered devices, including smartphones, laptops, and tablet computers, as well as embedded systems. However, ARM processors are also used for desktop computer, desktops and server (computing), servers, including Fugaku (supercomputer), Fugaku, the world's fastest supercomputer from 2020 to 2022. With over 230 billion ARM chips produced, , ARM is the most widely used ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Processor Registers
A processor register is a quickly accessible location available to a computer's processor. Registers usually consist of a small amount of fast storage, although some registers have specific hardware functions, and may be read-only or write-only. In computer architecture, registers are typically addressed by mechanisms other than main memory, but may in some cases be assigned a memory address e.g. DEC PDP-10, ICT 1900. Almost all computers, whether load/store architecture or not, load items of data from a larger memory into registers where they are used for arithmetic operations, bitwise operations, and other operations, and are manipulated or tested by machine instructions. Manipulated items are then often stored back to main memory, either by the same instruction or by a subsequent one. Modern processors use either static or dynamic random-access memory (RAM) as main memory, with the latter usually accessed via one or more cache levels. Processor registers are normally ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |